The Components
FireWall-1 can be broken down into three basic components:
A firewall module: A device that enforces a security policy. Also called an enforcement point.
A management module: A device that stores, compiles, and installs the security policy the firewall modules enforce. It also stores logs the firewalls send back and can send alerts.
SmartConsole: Programs that talk to a management module and allow you to view logs and system status, as well as modify the security policy. In NG FP2, this collection of programs are generally referred to as GUI Clients. Each component can exist on completely separate systems, or they all can exist on the same system. Figure 7.1 shows how the components communicate with one another.
Figure 7.1. Connections between various modules
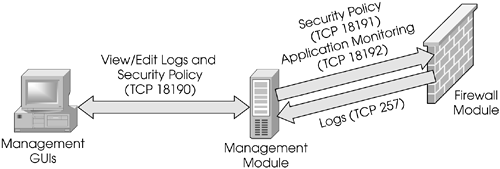
How do these processes communicate with each other? The GUI connects to the fwm process on the management module, which listens on TCP port 18190. The IP address of the client, as well as the username and password that are supplied, are authenticated against a database of allowed IP addresses and users. If these match, the connection is allowed. The network objects, security policies, and users are downloaded to the local GUI. Depending on the access privileges, the user can view logs and system status and read, modify, and load new security policies to the firewall modules. All communication between the management module and GUI are encrypted.
The management module stores configuration about your firewall modules. This includes network objects, users, security policies, and logs. It compiles and loads rulebases to the firewall modules. The management module opens connections to the remote firewalls via TCP port 18191 on demand to load security policies. Applications are monitored over TCP port 18192.
The firewall module enforces your security policy. It accepts, drops, rejects, authenticates, and encrypts traffic. The firewall module opens a connection to its management module on TCP port 257 to send logs. It also opens a connection via TCP port 18191 to fetch the security policy at boot time. In addition, the firewall module communicates with antivirus servers, URL filters, and authentication servers as necessary.
The communication between the management and firewall module is encrypted and authenticated by means of Secure Internal Communication (SIC).






