SecureClient Packaging Tool
Part of the problem with any sort of client-based VPN solution is getting the client installed and configured in the correct manner. Check Point makes this easier with the SecureClient Packaging Tool, which allows you to create your own preconfigured SecureClient installations. This makes the experience for the end user a much less confusing one. It's even possible to create totally "silent" installations, that is, ones that require no user prompts whatsoever and no dialog boxes.
When you start up the SecureClient Packaging Tool, you have to log in with a username and password similar to using SmartDashboard/Policy Editor, SmartView Tracker/Log Viewer, and other SMART Clients. In fact, none of these other GUIs can be active while the SecureClient Packaging Tool is connected to the management station.
The SecureClient Packaging Tool allows you to define a number of "profiles" that guide the SecureClient installation. By default, none are defined; you have to create one. Select New from the Profile menu or click on the New Profile button. You will be presented with a wizard dialog that will step you through the various options. Click on Next and you will see a dialog similar to Figure 12.31.
Figure 12.31. Naming the SecureClient profile
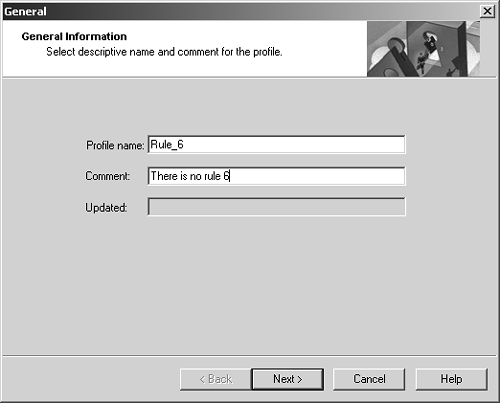
In this dialog, you specify a name and a comment for the profile. If you open an existing profile, this dialog will show the last date and time that profile was updated. Click Next. Figure 12.32 appears.
Figure 12.32. Choosing the default connection mode
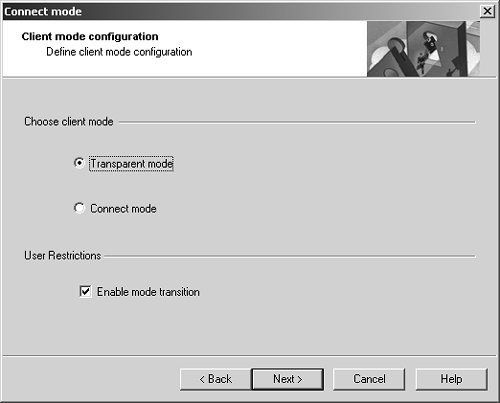
Here, you can choose which Connect Mode is the default and prevent an end user from being allowed to change that configuration (e.g., unchecking the "Enable mode transition"). Choose the options appropriate for your site and click Next. Figure 12.33 appears.
Figure 12.33. Choosing the security policy for clients
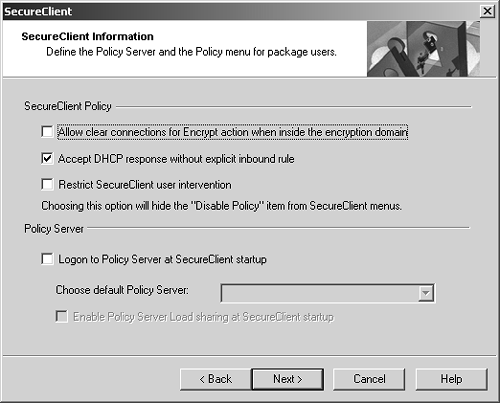
This screen presents the following options.
Allow clear connections for Encrypt action when inside the encryption domain: With this property enabled, any Desktop Security rules that have Encrypt as an action will also accept unencrypted traffic if the client has an IP address within the encryption domain.
Accept DHCP responses without explicit inbound rule: This permits inbound DHCP response packets without requiring a specific rule in the Desktop Security policy.
Restrict SecureClient user intervention: This prevents an end user from unloading the Desktop Security policy from his or her client. Specifically, it removes the entry from the menu that unloads the policy.
Logon to Policy Server at SecureClient startup: When SecureClient starts up, you can force a logon to the policy server. Choose the default policy server and (optionally) enable Policy Server Load Sharing. This option makes sense only in Transparent mode?Connect Mode always requires a logon to a policy server.
After you have configured these options, click Next to move to the screen shown in Figure 12.34.
Figure 12.34. Selecting additional SecureClient options
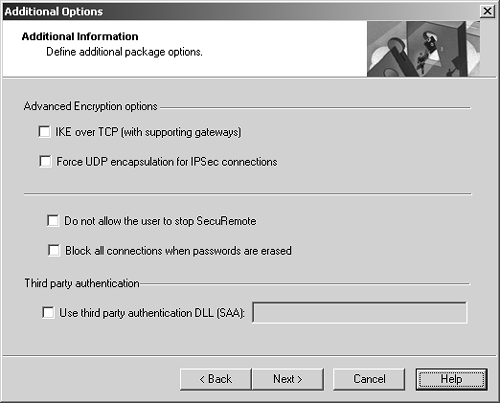
The options you can choose here are listed below.
IKE over TCP: Due to the fact that some home users' NAT routers do not deal with fragmented UDP packets very well and IKE Phase 1 packets can be fragmented, the option of doing IKE Phase 1 over TCP is supported. IKE Phase 2 is handled over UDP as usual.
Force UDP encapsulation for IPSec connections: By default, SecureClient resorts to UDP encapsulation (see FAQ 12.1 for details) only when the client is subject to NAT. To force the client to use SecureClient even when it is not behind a NAT device, check this box.
Do not allow the user to stop SecuRemote: This removes the Stop VPN-1 SecureClient option from the menu, which should prevent an unprivileged user from stopping SecureClient.
Block all connections when passwords are erased: All encrypted connections will be blocked when the Erase All Passwords option is chosen in SecureClient. This should force the end user to reauthenticate before continuing.
Use third party authentication DLL: If you have a DLL that uses Secure Authentication, put the name of the file here. This file should then be copied into your custom SecureClient installation package, described later in this chapter.
Choose the appropriate options and click on Next. A new screen appears (see Figure 12.35).
Figure 12.35. Setting SecureClient topology information
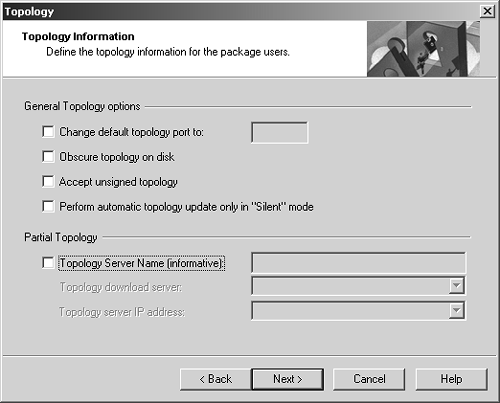
Here you can configure the following options.
Change default topology port to: If you wish to use a different port for allowing clients to download topology from TCP port 264, you can tell SecureClient which port to use. Note that you must make changes on your management station and firewall modules. See FAQ 12.7 later in this chapter for details.
Obscure topology on disk: Any topology information that exists in the userc.C file will be obscured (i.e., encrypted) so that it cannot be read by a human. However, SecureClient will be able to read it. Note that some parts of the file will remain unobscured (e.g., client options).
Accept unsigned topology: This allows the client to accept topology from any host without requiring any authentication. This is generally not recommended.
Perform automatic topology update only in "Silent" mode: When this box is checked, the client will request a site update at the time authentication is requested. This makes the topology update process much more transparent to the end user.
Partial Topology: If you make your installation package generally available (say, on the Internet), you might not want to include a full site topology in order to avoid making available any sensitive information. An alternative is to include a partial topology, which consists of a "friendly name" (the topology server "informative" name), a network object (select a firewall or gateway cluster from the pull-down menu), and the IP address the client will use to obtain policy. The first time the client authenticates, a proper topology will be downloaded.
After selecting the appropriate options, click Next. Figure 12.36 appears. If you are using Entrust Certificates, you can configure a certificate authority, select an LDAP server to use to provide information about certificates, and indicate whether or not to use the Entrust Entelligence software.
Figure 12.36. Defining certificate authority information
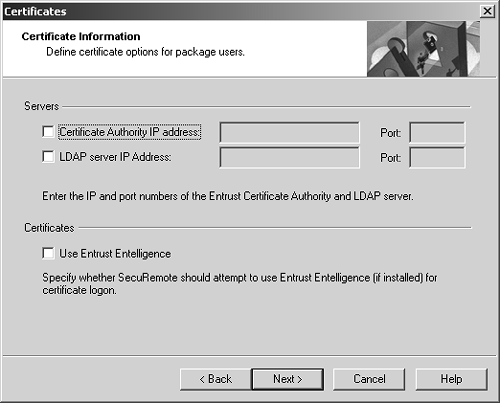
If you aren't using Entrust Certificates, click Next to move to the next screen (see Figure 12.37).
Figure 12.37. Configuring Silent Installation
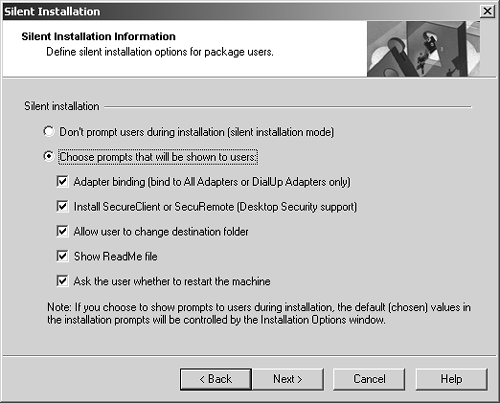
On the Silent Installation screen, you can choose to make the installation silent or use prompts for certain user options. In a silent installation, all the defaults chosen in the packaging tool will be used. If the end users are prompted, they will be given some choices, with the default values being what the packaging tool specifies. You still end up having to make a manual change to the product.ini file to prevent the display of the End User License Agreement (see the next subsection).
Once you have finished with the silent installation screen, click Next. Figure 12.38 shows the new screen.
Figure 12.38. Setting installation options
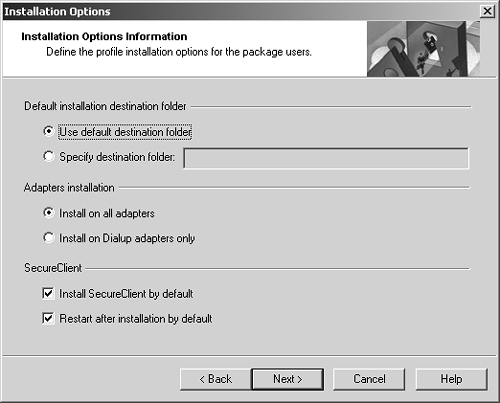
You can set the following additional installation options.
Default installation destination folder: If you select the default location, the software will be installed in C:\Program Files\CheckPoint\SecuRemote. If a different location is desired, you can select "Specify destination folder" and type in the appropriate path.
Adapters installation: You can have SecureClient installed either on the dial-up adapters only or on every adapter. Since SecureClient can be used only on network interfaces to which it is bound, this choice affects how SecureClient can be used. While the option is not available at install time, it is possible to disable SecureClient on specific adapters after the fact. In Windows NT, 2000, and XP, administrator rights are required to do this.
Install SecureClient by default: Select this option to install SecureClient with Desktop Security options. If unchecked, installation will include only the basic VPN functionality.
Restart after installation by default: Once installation is completed, the client platform should be rebooted so the software can load. This option determines whether or not that should be the option by default.
Select the appropriate installation options and click Next. Set the logon options shown in Figure 12.39.
Figure 12.39. Defining the operating system logon
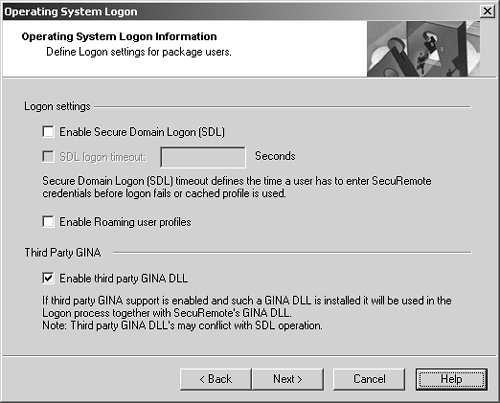
The options are described below.
Enable Secure Domain Logon (SDL): This option allows remote clients to establish a VPN connection before attempting to log into the domain. (See the Microsoft Networking and SecureClient section earlier in this chapter.)
SDL logon timeout: This option tells SecureClient how long it should wait for the client to enter authentication information before timing out and passing control back to the operating system, which will log you on with "cached credentials." This affects a parameter in the Windows registry that tells Windows how long to wait before giving up on attempts to talk to the domain controller.
Enable Roaming user profiles: In order for Roaming user profiles in Windows to work, SecureClient needs to keep the VPN connection operational for a period of time after the user logs off. Normally, the VPN connection is terminated once the client logs off. If this option is checked, the VPN will remain active for approximately 5 minutes after the user logs off.
Enable third party GINA DLL: If you are using other software that has its own GINA DLL file, you need to enable this option. This tells SecuRemote to try to cooperate with any GINA DLL file it finds and to attempt to "chain" to other GINA DLL files. However, this option doesn't always work, so you should test this carefully.
Once you have chosen the appropriate options, click on Next. The screen shown in Figure 12.40 appears.
Figure 12.40. Almost finished with the SecureClient Packaging Tool
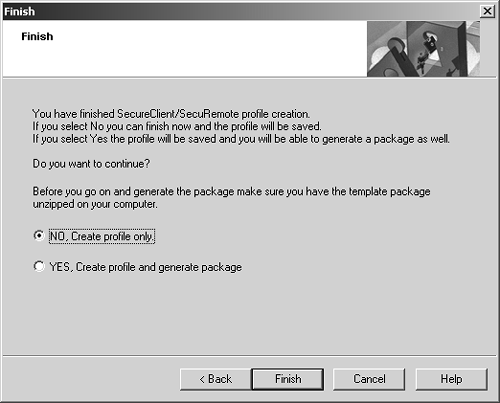
If you have the appropriate version of SecureClient decompressed on your platform and you're ready to generate a package, select YES and click Next. If you haven't yet downloaded the Configurable versions of SecureClient and decompressed them for each platform type on which you wish to install SecureClient, select NO and click Next. Figure 12.41 shows what happens if you select YES and click Next or if you select the profile and then select Generate from the Profile menu.
Figure 12.41. Generating the package
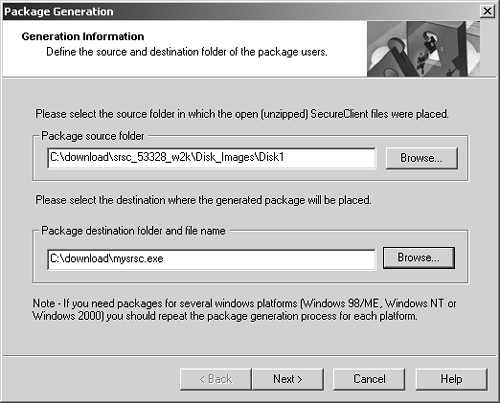
Select the appropriate location where the decompressed SecureClient installation is, specify where you want the generated executable file to reside, and click Next. This generates your installation file.
Manually Creating an Installation Image
Most of the options you can select in the SecureClient Packaging Tool can be specified in the product.ini file as well. If you change options in this file and use your own userc.C file instead of a custom one, you can make your own installation package. All you need is some method of generating a self-expanding archive and having it run setup.exe.
The following product.ini entries are relevant to FireWall-1 NG. Unless otherwise specified, you can also set these options in the SecureClient Packaging Tool. Note that most of these options are binary, that is, they can be set with either a 1 or a 0. In most cases, the default values in the file are shown and the effect of changing from the default is described.
ShowWelcome=1: Suppresses the Welcome to Check Point SecureClient screen upon installation if set to 0.
ShowLic=1: Suppresses the display of the End User License Agreement if set to 0. This option cannot be set in the SecureClient Packaging Tool.
OverwriteConfiguration=0: Indicates that, when a previous version of SecureClient is detected, the default should be to upgrade the configuration if this option is set to 0. Overwrite will be the default if this option is set to 1.
ShowUpdateOverwrite=1: Does not present the end user with the choice of whether or not to overwrite the previous configuration if this option is set to 0. Instead, the client will use the default specified in the previous option.
PathAskUser=1: Asks the end user where the software should be installed if set to 1. If set to 0, the client will be installed in the default location, which is C:\Program Files\CheckPoint\SecuRemote.
DesktopSecurityDefault=1: Specifies whether this is a SecuRemote install (set to 0) or a SecureClient install (set to 1) by default, that is, whether or not to include the Desktop Security options.
DesktopSecurityAskUser=1: Does not prompt the user about Desktop Security if set to 0 and uses the previous option to determine whether to install SecuRemote or SecureClient.
InstallDialupOnly=0: Configures the usual default to install on all interfaces if set to 0. If set to 1, the default will be to install only on dial-up interfaces.
ShowNetworkBindings=1: Does not prompt the end user about whether to install on all interfaces or just dial-up ones if set to 0. Instead, the previous option will specify the installation on interfaces.
ShowReadmeFile=1: Suppresses the request to display the readme.txt file if set to 0.
EnableSDL=0: Enables Secure Domain Logon by default if set to 1.
SupportFWZ=0: Supports FWZ on the client if set to 1. Deprecated for NG FP2 and later.
OverwriteEntINI=0: Overwrites the entrust.ini file (if it exists) if this option is set to 1.
IncludeBrandingFiles=0: Includes a custom logo.bmp file, which replaces the Check Point logo everywhere, if set to 1.
Support3rdPartyGina=1: Attempts to chain with other GINA DLL files that might exist if set to 1. This is especially critical if you use Secure Domain Logon. If set to 0, no attempt to chain with other GINA DLL files will be made.
MajorVersion=5: Specifies the major version of SecureClient. NG is version 5.
MinorVersion=3: Specifies the minor version of SecureClient. For Feature Pack 3, it's 3. For NG AI, it's 4.
EnablePolicyView=1: Allows the end user to view the security policy pushed to their client if set to 1.
EnableLogView=1: Allows the end user to look at the local SecureClient logs if set to 1.
EnableDiagnosticsView=1: Allows the end user to view diagnostic information in SecureClient if set to 1.
EntrustSupport=1: Enables Entrust support if set to 1. Support is disabled if this option is set to 0.
ShowDriverSignatureWarning=1: Suppresses driver signature warnings (which might occur in Windows 2000 and XP during installation) if this option is set to 0.
MakeServiceNonInteractive=0: Allows the service to run in an unattended automated state (i.e., does not require a user to log on) if set to 1.
ShowRestart=1: Does not ask the end user to restart upon completion of installation if set to 0.
RestartAfterInstall=1: Specifies whether or not to default to a restart after installation. If the previous option is set to 0 and this option is set to 1, the end user's machine will be rebooted without prompting.






