SmartView Tracker
In FireWall-1 NG FP2 and before, the application is called the Log Viewer or Log Manager. In NG FP3 and later, it is called SmartView Tracker. I discuss SmartView Tracker specifically in this section. Figure 5.8 shows how SmartView Tracker looks after you authenticate.
Figure 5.8. SmartView Tracker
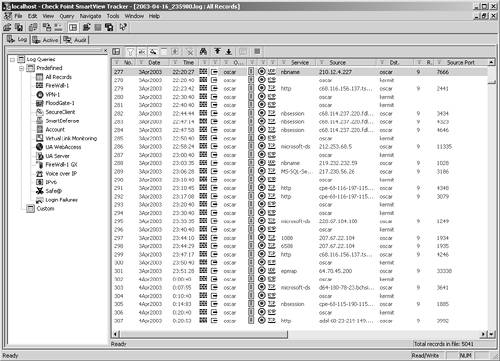
When you load up the SmartView Tracker, you will see a number of things. Along the top of the screen, three tabs are shown: Log, Active, and Audit. Log is for rulebase and event logging from Check Point modules, Active means currently active connections, and Audit is for logging the actions of administrators.
Table 5.8 shows the various log fields used by FireWall-1, VPN-1, SecureClient, and SmartDefense.
Entry | Description |
|---|---|
No. | The log entry number. |
Date | The date the log entry was generated. |
Time | The time the log entry was generated. |
Product | The product for which this log entry is relevant. |
Interface | The interface on which the packet being logged came in or went out (with direction) or indicates "daemon" if the message came from a FireWall-1 daemon (e.g., the security servers, fwm). |
Origin | The firewall module that generated the log entry. |
Type | Log (normal rulebase logging), Alert (for alert log entries), or Control (changes to policy or logging on a firewall). |
Action | The action taken on the packet (Drop, Reject, Accept, and so on). |
Service | The service of the packet (HTTP, Telnet, and so on), which is usually based on the destination TCP/UDP port. |
Source | The source IP address of the connection or packet. |
Destination | The destination IP address of the connection or packet. |
Proto | The protocol of the IP packet (TCP, UDP, ICMP, and so on). |
Rule No. | The rule number that this connection or packet matched in the rulebase. |
NAT rule num. | The NAT rule number that this connection or packet matched in the rulebase. |
Nat add. rule num. | The number of an additional NAT rule if one was applied. |
Source Port | The source port of the packet if TCP or UDP. For other protocols, this field is gibberish. |
User | The appropriate username if the action was an authorization or deauthorization or was the result of an authenticated connection (with or without encryption). |
SrcKeyID | The source's KeyID if the action was encrypt or decrypt. |
DstKeyID | The destination's KeyID if the action was encrypt or decrypt. |
Elapsed | The amount of time the connection was active (Accounting mode only). |
Bytes | The number of bytes for the connection in question (Accounting mode only). |
XlateSrc | The source IP address the connection will have after NAT is applied. |
XlateDst | The destination IP address the connection will have after NAT is applied. |
XlateSPort | The source port the connection will have after NAT is applied. |
XlateDport | The destination port the connection will have after NAT is applied. |
Partner | The name of the partner site making a connection if an extranet is defined. |
Community | The name of the community to which this log entry relates if a VPN Community is used. |
Enc Scheme | The encryption scheme used for this connection (usually IKE, but may be others if managing FireWall-1 4.1 boxes). |
VPN Peer Gateway | The gateway that sent or received the encrypted packet. |
IKE Initiator Cookie | Information relating to the IKE communication. |
IKE Responder Cookie | Information relating to the IKE communication. |
IKE Phase 2 Msg Id | The ID of the IKE negotiation. |
Encryption Methods | Lists all the encryption methods used in both encryption and data integrity. |
Info | More information about this log entry. For most packets or connections, it will simply show "len X," where X is the number of bytes in the packet. This entry also shows useful information on encrypt/decrypt log entries and drops or rejects on Rule 0. |
If you have a serious amount of traffic flowing through the firewall, you will have many log entries. It is very important that you examine your logs on a regular basis to make sure that proper security is maintained. However, it can be difficult to look through a few thousand log entries. The following list contains a few hints that might save you some time.
Limit the number of entries that appear in the log. Do not log on every rule, but instead log judiciously. Log only important information (e.g., all unauthorized traffic). Creating rules to catch noise services to drop and not log is one way to do this.
Rotate your logs frequently. The SmartView Tracker/Log Viewer does not function very well when the log contains more than a few hundred thousand entries. Although you can rotate your logs manually in the GUI, it is recommended that you set up log rotation on a schedule. This is discussed in the Log Maintenance section later in this chapter.
Use the selection criteria to limit the displayed items or to find the entries you are most interested in.
Use some of the third-party log analysis tools listed in Appendix G.
Selection criteria are chosen by right-clicking the column title in question and selecting Edit Filter. The options presented depend on the field you click. The following list contains a few notes regarding selection criteria.
Selection criteria are cumulative; if you use more than one selection criteria, they will be ANDed together.
The SmartView Tracker/Log Viewer remembers previous selection criteria, so you could possibly end up excluding all log entries. Before applying selection criteria, click the Current Selection Criteria button, and make sure all the selection criteria are deleted if necessary.
The option Show Null Matches on the Options screen affects how log entries are displayed in the selection criteria. You will see Show Null Matches as an icon above the log entries in FireWall-1 NG FP3 or in the Options section under the Selection menu. This shows entries that are neither included nor excluded by the current selection criteria. For example, if you are selecting entries based on the Action field and you have control entries in your log, they will neither be included nor excluded because control log entries do not have Action entries.
Right above the list of log entries are three icons that control whether or not the selection criteria are applied, whether or not IPs are resolved to names, and whether or not services are resolved to names. In FireWall-1 NG FP1 and FP2, these are listed under the Tools menu.
Viewing Logs from the Command Line
You can also view logs from the command line on the management module by using the command fw log. This command shows the logs in ASCII text. Note that not all fields are shown, only relevant fields. Check Point has improved the output of this command so that it is easier to read. It should also be easier to parse with a variety of tools. Output from fw log looks something like this:
Date: Aug 24, 2002 1:15:02 ctl craig.phoneboy.com >daemon sys_message: installed defaultfilter; product: VPN-1 & FireWall-1; 1:15:02 ctl craig.phoneboy.com >daemon sys_message: The eth-s3p1c0 interface is not protected by the anti-spoofing feature. Your network may be at risk; product: VPN-1 & FireWall-1; 1:15:02 ctl craig.phoneboy.com >daemon sys_message: The eth-s2p1c0 interface is not protected by the anti-spoofing feature. Your network may be at risk; product: VPN-1 & FireWall-1; 1:15:02 ctl craig.phoneboy.com >daemon sys_message: The eth-s1p1c0 interface is not protected by the anti-spoofing feature. Your network may be at risk; product: VPN-1 & FireWall-1; 1:43:20 ctl craig.phoneboy.com >daemon sys_message: installed phoneboy-traditional; product: VPN-1 & FireWall-1; 1:43:20 craig.phoneboy.com >daemon cp_message: Parameter 'Connections hash table size' changed from 65536 to 32768; 12:34:08 drop craig >eth-s2p1c0 product: VPN-1 & FireWall-1; src: Alpha-Cluster-Inside.foo.com; s_port: IKE; dst: craig; service: 876; proto: udp; rule: 5; 12:48:17 accept craig >eth-s1p1c0 product: VPN-1 & FireWall-1; src: cartman.phoneboy.com; s_port: 2343; dst: craig; service: https; proto: tcp; rule: 1; 12:48:22 accept craig >eth-s1p1c0 product: VPN-1 & FireWall-1; src: cartman.phoneboy.com; s_port: 2344; dst: craig; service: https; proto: tcp; rule: 1; 12:48:55 accept craig >eth-s1p1c0 product: VPN-1 & FireWall-1; src: cartman.phoneboy.com; s_port: 2345; dst: craig; service: https; proto: tcp; rule: 1;
There are plenty of options you can use with fw log to help you find the log entries you want to examine. Table 5.9 lists the options for this command. Here's the usage information for the fw log command:
fw log [-f [-t]] [-n] [-l] [-o] [-c action] [-h host] [-s starttime] [-e endtime] [-b starttime endtime]
Flag | Description |
|---|---|
-f | Shows the log forever if no file is specified. Entries are shown as they are generated. |
-t | Used with -f to show only new log entries (i.e., entries added after fw log was executed). |
-l | Includes the date in each line's log entry instead of printing out the date separately. |
-s start-time | Used with -f to show log entries generated after the specified date or time (hh:mm format). |
-e end-time | Used with -f to show log entries generated before the specified date or time (hh:mm format). |
-b timea timeb | Used with -f to show log entries generated between the specified times. |
-o | Shows detailed log chains, i.e., all entries in a log record. |
-c action | Shows only entries of a specific action type: accept, drop, reject, ctl. |
-u filename | Specifies the unification scheme file name. |
-m mode | Specifies the unification mode: semi, raw, initial. The latter is the default. |
-a | Shows only accounting log entries. |
-k alert-type | Shows only the specified alert_type (or all). |
-g | Prevents delimiting of the displayed log entries, i.e., uses no colon (:) after a field name or semicolon (;) after a field value. |
-h firewall | Shows log entries generated by the firewall module named "firewall." |
-n | Prevents name resolution for source and destination IP addresses. |
log-file | Uses the specified log file (otherwise, use $FWDIR/log/fw.log). |
[-u unification_scheme_file] [-m (initial|semi|raw)] [-a] [-k (alert_name|all)] [-g] [logfile]
Viewing Rules in SmartDashboard
When right-clicking on a log entry in SmartTracker in FireWall-1 NG FP3 and above, you have the option of selecting View Rule in SmartDashboard. This is useful because it allows you to see exactly which rule the logged packet hit. However, this works only if the currently installed security policy has a Database Revision associated with it. In SmartDashboard, select File 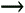
Future Accept log entries can be selected in SmartDashboard and the View Rule in SmartDashboard function will work.
Active Mode and Blocking Connections
So far, I have discussed only the most commonly used mode: Log mode. In the Log Manager application (NG FP3 and later), along the top of the screen beneath the icon bar is a series of tabs. In NG FP2 and before, there is a pull-down menu in the icon bar. Either mechanism allows you to change to the other two modes in the Log Viewer: Active and Audit. Because Active mode works differently than Log mode, let's take a look at how it works. Figure 5.9 shows a screen from Active mode. This mode shows connections that are currently active through the firewall (i.e., in its state tables). Table 5.10 lists the fields that are displayed and provides descriptions of each field.
Figure 5.9. Active mode in Log Manager
Name | Description |
|---|---|
No. | The log entry number. |
Date | The date the log entry was generated. |
Time | The time the log entry was generated. |
Conn. ID | A number referencing this specific connection. |
Product | The product this connection is relevant for. |
Interface | The name of the interface the packet came in on. Usually "daemon." |
Origin | The firewall module that generated the log entry. |
Type | Usually Log. |
Action | The action taken on the packet, usually Accept. |
Service | The service of the packet (HTTP, Telnet, and so on), which is usually based on the destination TCP/UDP port. |
Source | The source IP of the packet. |
Destination | The destination IP of the packet. |
Proto | The IP protocol of the packet. This is usually TCP, UDP, or ICMP, but it could be any IP protocol or a number. |
Source Port | The source port of the packet if it is TCP or UDP. |
Elapsed | The amount of time elapsed since the connection began, for entries logged as type Accounting. |
Bytes | The number of bytes that have elapsed since the connection began, for entries logged as type Accounting. |
Information | More information about the entry. This is usually blank. |
The main function you can perform in Active mode is to temporarily block a connection. This is done without modifying the existing rulebase in Smart Dashboard/Policy Editor. All such blocks are active until the firewall module is unloaded (e.g., with fw ctl uninstall), the system is rebooted, or the block is manually removed. To block a specific connection, click on the connection, then pull down Block Intruder from the Tools menu. You will be presented with the following options.
Block only this connection: Blocks only this specific connection. If the host attempts to connect to this destination and this service port again, it will be blocked.
Block access from this source: Blocks any connection the host listed as the source attempts to make.
Block access to this destination: Blocks the connection if any host tries to reach this destination host.
Blocking Timeout: Indicates how long this block will be active. Indefinite really means until the firewall module is unloaded (via fw ctl uninstall), a reboot occurs, or the connections are unblocked by using fw sam ?D or fw sam ?C, or by selecting Clear Blocking under the Tools menu.
Force this blocking: Indicates the firewalls that will enforce the block you are requesting. By default, only the firewall the connection went through will enforce this block. This function can be pushed to all firewalls managed by this management console.
Note that you can enable these actions from the command line of the management module or firewall module using the command fw sam, as shown below. These command options are described in Table 5.11.
sam [-v] [-s sam-server] [-S server-sic-name] [-t timeout]
[-l log] [-f fw-host] [-C] -((n|i|I|j|J) <criteria>
sam [-v] [-s sam-server] [-S server-sic-name] [-f fw-host]
-M -ijn <criteria>
sam [-v] [-s sam-server] [-S server-sic-name] [-f fw-host] -D
Option | Description |
|---|---|
-v | Turns on verbose mode. |
-s sam_server | Specifies the Suspicious Activity Monitoring (SAM) server to be contacted. The default is localhost. |
-t timeout | Specifies the timeout in seconds. The default is Never. |
-f fw_gist | Specifies the firewalls to run the operation on. This command option should contain either the name of a firewalled object, the name of a group of firewalled objects, or one of the predefined names: all and gateways. The default is all. |
-C | Cancels the specified option. |
-n | Notifies every time a connection that matches the specified criteria passes the firewall. |
-i | Inhibits connections that match the specified criteria. |
-I | Inhibits connections that match the specified criteria and closes existing connections that match it. |
-D | Deletes all previous operations. |
The criteria for the fw sam command are described in Table 5.12.
The IP addresses in Table 5.12 may be resolvable hostnames or dotted decimal notation addresses. Service may be a resolvable service name (in the services file, like Telnet or WWW) or a service number (a TCP/UDP port number). Protocol may be a protocol name (like TCP) or a protocol number.
Format | Description |
|---|---|
src ipaddr | Matches the source address of connections |
dst ipaddr | Matches the destination address of connections |
any ipaddr | Matches the source or destination address of connections |
subsrc ip netmask | Matches the specified network by IP and netmask in the source IP of the packet |
subdst ip netmask | Matches the specified network by IP and netmask in the destination IP of the packet |
subany ip netmask | Matches the specified network by IP and netmask in either the source or destination IP of the packet |
srv srcip dstip service protocol | Matches the specified source, destination, and service |
subsrv srcip netmask dstip netmask service protocol | Matches the specified source network (IP and netmask), specified destination network (IP and netmask), service, and protocol (i.e., blocks a service between two networks) |
subsrvs srcip netmask dstip service protocol | Matches the specified source network (IP and netmask), specified destination host, service, and protocol (i.e., blocks a specific network from accessing a particular host via a particular port/protocol) |
subsrvd srcip dstip netmask service protocol | Matches the specified source IP, specified destination network (IP and netmask), service, and protocol (i.e., blocks a specific host from accessing a particular network using a specific port/protocol) |
dstsrv dstip service protocol | Matches the specified destination IP, service, and protocol (i.e., blocks all access to a specific host via a specific port/protocol) |
subdstsrv dstip netmask service protocol | Matches the specified source network (IP and netmask), service, and protocol (i.e., blocks all access to a specific network via a specific port/protocol) |
srcpr ip protocol | Matches the specified source IP address and protocol (i.e., prevents a particular IP from originating traffic of a specified protocol type) |
dstpr ip protocol | Matches the specified destination IP address and protocol (i.e., prevents all access to a particular host via the specified protocol) |
subsrcpr ip netmask protocol | Matches the specified source network (IP and netmask) and protocol (i.e., prevents a particular network from originating traffic of a specified protocol type) |
subdstpr ip netmask protocol | Matches the specified destination network (IP and netmask) and protocol (i.e., prevents all access to a particular network via the specified protocol) |
For example, if you wanted to turn on additional notification for a specific action, say, accessing www.phoneboy.com, you would type:
# fw sam -n dst www.phoneboy.com
All notifications will appear as rule "sam" in the logs. If you wanted to deny all connections to www.phoneboy.com for 60 seconds, you would type:
# fw sam -t 60 -i dst www.phoneboy.com
If you wanted to deny all connections to foo.bar.com and close any existing connections, you would type:
# fw sam -I dst foo.bar.com
If you wanted to close a specific Telnet connection from host.yoursite.com to foo.bar.com and prevent further requests from that host, you would type:
# fw sam -I srv host.yoursite.com foo.bar.com 23 6
(Note that 23 is the port number for Telnet; 6 is the protocol number for TCP.) To cancel the preceding operation, you would type:
# fw sam -C srv host.yoursite.com foo.bar.com 23 6
To cancel all previous operations (i.e., unblock all blocked connections), you would type:
# fw sam ?D
Audit Mode
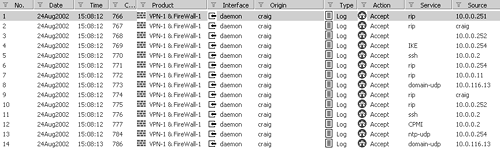
A new feature in NG is the ability to see exactly what administrators do in the various SmartConsole applications. The most detail is shown for SmartDashboard/Policy Editor because that is where the most changes can be made. For the other GUIs, you will see when administrators log in or out only. Figure 5.10 shows a sample of Audit mode. Table 5.13 explains the fields you will see in this view.
Figure 5.10. SmartView Tracker, Audit mode
Entry | Description |
|---|---|
No. | The log entry number |
Date | The date the log entry was generated |
Time | The time the log entry was generated |
Origin | The management module that generated the log entry |
Application | The product for which this log entry is relevant |
Operation | The event that is being logged (Logged in, Logged out, Create, Update, Install Policy) |
Object Name | The object that was acted upon, if relevant |
Changes | The changes that occurred to this object in detail |
Administrator | The administrative user making the change |
General Information | Other relevant information (e.g., user logged in, which policy was loaded) |






