Frequently Asked Questions
Now that you have learned the basics of setting up authentication, take a look at the following FAQs for more information. As in previous chapters, the FAQs are numbered for easy reference.
8.1 How Do I Use Users in an Authentication Server without Entering Them into FireWall-1?
Because of the way you configure LDAP into FireWall-1, all LDAP users in the appropriate branch will appear in SmartDashboard automatically. However, if you are using RADIUS, SecurID, Defender, TACACS, or even a Windows NT domain, you need to create an external user profile in NG FP3 or later or a user with the username generic* in NG FP2 and earlier (only one such user can be defined). FireWall-1 queries the external authentication mechanism defined in the external user profile or in generic* user for users who are not defined in FireWall-1. You configure this user as you would any other user, keeping in mind that the parameters you set apply to all users not otherwise defined in FireWall-1. For users who require different parameters (for example, those who need to be in different groups), you still need to define these users individually in FireWall-1.
8.2 How Do I Integrate FireWall-1 into a Windows NT Domain?
If you have FireWall-1 on Windows NT, you can simply make the firewall system part of your Windows NT domain and set up an external user profile or generic* user to use OS Authentication. However, it is generally not recommended that you run any of the Microsoft Networking services on your firewall.
If your FireWall-1 does not run on Windows NT or you decide not to run the Microsoft Networking services on your Windows NT firewall, you can set up a RADIUS server that pulls its authentication information from Windows NT, which requires running a RADIUS server on a Windows NT server. You can easily set up FireWall-1 to authenticate against the RADIUS server. This configuration is far more secure than running Microsoft Networking services on your Windows NT firewall.
8.3 How Do I Allow People Access Based on Their Windows Usernames?
This involves using a product by Check Point called Meta IP, which is not covered in this book. For more details on this product, visit Check Point's Web site at http://www.checkpoint.com.
8.4 How Do I Import or Export Users from a FireWall-1 User Database?
The commands in question are fw dbimport and fw dbexport, respectively. The options for fw dbimport are described in Table 8.3. The usage is as follows:
fw dbimport [-m] [-s] [-v] [-r] [-k errors] [-f file] [-d delim]
Parameter | Description |
|---|---|
-m | Applies if an existing user is encountered in the import file. If this option is specified, the user's default values will be replaced by the values in the template (the default value or the value given in the attribute list for that user in the import file), and the original values will be ignored. If this option is not specified, an existing user's original values will not be modified. |
-s | Suppresses the warning messages issued when an existing user's values are changed by values in the import file. |
-v | Enables verbose mode. |
-r | Deletes all existing users (but not groups or templates) in the database. |
-k nerrors | Continues processing until nerrors errors are encountered. The line count in the error messages starts from 1 including the attributes line and counts empty or commented-out lines. |
-f file | Specifies the name of the import file. The default import file is $FWDIR/conf/user_def_file. |
-d delim | Specifies a delimiter different than the default value (;). |
Parameter | Description |
|---|---|
-g usergroup | Specifies a group of users to be exported (others are not exported). |
-u username | Specifies that only the indicated user should be exported. |
-d delimiter | Specifies a delimiter different than the default value (;). |
-a attributes | Specifies the attributes to export in the form of a comma-separated list between {} characters, e.g., -a {name,days}. If there is only one attribute, the {} may be omitted. |
-f filename | Specifies the name of the output file. The default output file is $FWDIR/conf/user_def_file. |
The fw dbexport options are documented in Table 8.4. The usage is as follows:
fw dbexport [ [-g <group> | -u <user>] [-d <delim>]
[-a {attrib1, attrib2, ...} ] [-f <file>] ]
NOTE!
FireWall-1 Passwords are stored in the output encrypted with the UNIX crypt() function using the first two characters of the actual password as the "salt" argument. |
NOTE!
The fw dbimport function will not import users who are assigned to groups that do not exist in the user database. You need to create these groups manually before importing the users. |
8.5 How Do I Add My Own Custom Message for Authentication?
Go to the Security Servers frame of the Global Properties screen, which is shown in Figure 8.51. You can specify welcome files for Telnet, FTP, rlogin, and Client Authentication. Specify the full path to the file, which must exist on the firewall module.
8.6 How Do I Forward Authenticated HTTP Requests to an HTTP Proxy?
In the Authentication frame of the Gateway Properties screen (see Figure 8.28 earlier in the chapter), there is a checkbox labeled Use Next Proxy. If you want FireWall-1 to send requests to a proxy server, fill in the host and the port number of the proxy server. Note that this works only when FireWall-1 is configured as the proxy server for your Web-browsing clients.
8.7 Can I Use FireWall-1 as a Reverse HTTP Proxy?
Yes, you can. The instructions for enabling this are almost exactly the same as the instructions for setting up Clientless VPN except that you can use the HTTP service instead of HTTPS. Authentication is still required.
8.8 How Do I Remove the Check Point Banner from Authentication?
The authentication daemons all show a banner identifying them as Check Point firewalls. Some people, at least those who believe in the concept of "security through obscurity," think that it is not a good idea to reveal the kind of firewall you are running. You can remove these banners by changing a parameter in objects_5.0.C (see FAQ 4.2 for details). The following commands would be entered into dbedit:
dbedit> modify properties firewall_properties undo_msg true dbedit> update properties firewall_properties
WARNING!
If you use the FTP or SMTP Security Server, connections may fail after you disable the banner messages if you don't define a custom message for these servers as described in FAQ 8.5. |
8.9 Can I Use FireWall-1 as a Proxy?
FireWall-1 can authenticate these connections without having to proxy. There may be environments where using FireWall-1 in a proxy capacity is necessary. FireWall-1 requires authentication for Telnet, FTP, and rlogin. HTTP can be used as a proxy without authentication using a resource.
For proxy mode to work correctly, you must enable the Prompt for Destination mode in objects_5_0.C. This is described earlier in the Clientless VPN section.
For HTTP, if you do not want to perform authentication but want to use HTTP in proxy mode, you need to create a matchall resource, as discussed in Chapter 9, and use HTTP with this resource instead of just HTTP.
8.10 Can I Use FireWall-1 as an FTP Proxy for My Web Browser?
FireWall-1 supports proxying FTP using an FTP interface. However, Web browsers expect the FTP proxy to act like an HTTP proxy. Make sure you set your browser's FTP proxy to the firewall on port 80 instead of port 21.
Note that because FireWall-1 can be used as an FTP proxy with User Authentication, FTP or HTTP cannot be denied from the firewall because the firewall has to originate these connections.
8.11 How Do I Authenticate HTTP over Different Ports?
You need to follow these five steps to enable filtering on other ports.
Create a service for the ports in question (e.g., http8000).
Add a rule with the new service.
Reconfigure $FWDIR/conf/fwauthd.conf.
Install the security policy.
Bounce the firewall (cprestart)
The following paragraphs describe the steps in more detail.
Creating the service is straightforward. Create a new service of type TCP. Set the port accordingly (e.g., 8000). Go to the Advanced settings frame, and set the protocol type to HTTP.
To reconfigure $FWDIR/conf/fwauthd.conf, you need to add a line to this file for each port on which you want to filter. For port 8000, for instance, the line would read:
8000 fwssd in.ahttpd wait 0
Reinstall the security policy and bounce the firewall after making these changes (e.g., cprestart). You can then use HTTP port 8000 in a service, authenticate against it with User Authentication, and perform content security on that port.
8.12 How Do I Authenticate Outbound HTTPS Traffic?
FireWall-1 can authenticate outbound HTTPS traffic. However, it can do so effectively only when FireWall-1 is the proxy server for HTTPS requests from the Web browser. The following line must be added to $FWDIR/conf/fwauthd.conf:
443 fwssd in.ahttpd wait 0
This line ensures that the HTTP Security Server is listening on port 443 to handle HTTPS requests. Once this line is added to fwauthd.conf, FireWall-1 must be restarted (cprestart). Next, modify the HTTPS server so that the protocol type is HTTP (instead of None). You should then be able to add the appropriate rule and install the policy.
Note that no special certificate is necessary to authenticate outbound traffic.
8.13 Can I Authenticate Access to Internal HTTPS Servers?
Yes, you can. However, if you have Clientless VPN enabled, that will override the steps described below.
Make sure a certificate is generated in the VPN portion of your gateway object.
Modify $FWDIR/conf/fwauthd.conf so that the HTTP Security Server is running in SSL mode with your defined certificate.
Kill fwd on the firewall module.
Modify the HTTPS service to be of type HTTP.
Add an appropriate rule and install the security policy.
The following paragraphs describe the steps in more detail.
Go to the VPN frame of your gateway object. Generate a certificate against your certificate authority if needed. Make note of the certificate name (defaultCert if you allow the system to generate one for you).
Next, modify the file $FWDIR/conf/fwauthd.conf by adding a line that enables the HTTP Security Server to run on an additional service port dedicated to HTTPS:
443 fwssd in.ahttpd wait 0 eb:defaultCert
The eb:defaultCert at the end of this line means two things: encrypt between both the client-to-firewall connection as well as the firewall-to-server connection, and defaultCert refers to the name of your certificate. Once this change is made, use the command fw kill fwd on the firewall module. Assuming cpwatchdog is running, fwd should restart on its own in a minute or two.
Next, you have to set a few parameters in objects_5.0.C on the management station (see FAQ 4.2 for details). Enter the following commands into dbedit:
dbedit> modify properties firewall_properties http_connection_method_proxy true dbedit> modify properties firewall_properties http_connection_method_transparent true dbedit> modify properties firewall_properties http_connection_method_tunneling true dbedit> update properties firewall_properties
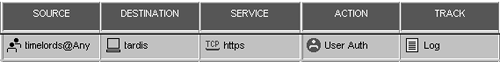
Modify HTTPS Service Properties so that the protocol type is HTTP. Add an appropriate rule to the rulebase (such as the rule shown in Figure 8.53), and install the security policy.
Figure 8.53. Sample User Authentication rule with HTTPS
NOTE!
When you connect to the server, you will get a message about the certificate not matching the name. Just accept the certificate when prompted. This is unavoidable. |
WARNING!
In NG FP3 base (no hotfixes), certificates from the ICA cannot be used with a Netscape/Mozilla browser. If you want Netscape browsers to work, you must use certificates from a different certificate authority or upgrade to Hotfix-2 or above. |
8.14 How Can I Authenticate with HTTP to a Site Requiring Its Own Authentication?
Enter your login as follows: remoteuser@fw1user. Then enter your password as follows: remotepass@fw1pass. FireWall-1 will strip off the @fw1user and @fw1pass portions when passing the authentication to the remote site. If the remote username or password contains an @, you need to enter the @ twice (e.g., @@).
8.15 How Can Users Change Their Own Passwords?
The short answer is they can't, at least not directly. One site I know of uses OS Password as its authentication mechanism. The company then allows its users to Telnet to the firewall, authenticate, and then change their passwords via the operating system of the firewall. This has all kinds of potential security risks involved, so it is not recommended.
If you are using an external authentication server and it has its own remote password-changing utility, you may be in luck. Check Point also supports enforcing password changes for LDAP users as long as the password is changed when prompted by FireWall-1 or is changed through SmartDashboard/Policy Editor. You may also be able to use the data from an fw dbexport, massage it with another application that allows you to change your password, and import it with fw dbimport.
8.16 Can a User Reset His or Her Own S/Key Chain?
When a user has fewer than ten S/Key passwords left, FireWall-1 will prompt the user to create a new S/Key chain if the user authenticates via Telnet, rlogin, or Client Authentication. The user will need to specify a different seed value (the default seed is the username), a new chain length to FireWall-1, and the last password in the chain.
On a UNIX machine, you would generate the new key chain as follows (assuming you want to use seed as the new seed value and 1000 as the chain length):
$ key 1000 seed Reminder - Do not use this program while logged in via telnet or rlogin. Enter secret password: foobar JOG WAKE SUN MEND ILL COWL
After generating the new key chain, you can input this information into your Telnet User Authentication or Client Authentication session as follows:
Check Point FireWall-1 authenticated Telnet server running on mrhat User: phoneboy SKEY CHALLENGE: 9 phoneboy. Enter SKEY string: MUG EMMA PI PRY HOYT MANN User phoneboy authenticated by S/Key system You have only 8 one-time passwords left. A new S/Key chain should be created. If you have a new chain, you can enter it now by typing the chain length and the last password in the chain. Enter New Chain (y/n) ? y Enter S/Key chain length: 1000 Enter the last string of the new chain: JOG WAKE SUN MEND ILL COWL New S/Key chain accepted Connected to foo
The password generated and entered in the preceding example is used only to initialize the S/Key chain. Future passwords will decrement from that point in the chain. Also, FireWall-1 always prompts you to use the old seed value, not the new one you entered. You need to remember to use the new seed value when using an S/Key generator or when generating your own list.
8.17 Can I Customize the HTTP Client Authentication Pages?
It may be desirable for a variety of reasons to customize these pages with a different look. The HTML files that FireWall-1 uses are located in $FWDIR/conf/ahclientd on the firewall module.
ahclientd1.html is the first page users are greeted with (i.e., this page prompts users for a username).
ahclientd2.html is the end-of-session page after a successful authentication.
ahclientd3.html is the page for signing off.
ahclientd4.html is the successful-login page where users choose the kind of sign-on or sign-off they desire.
ahclientd5.html is the Specific Sign-On page.
ahclientd6.html is the page for authentication failure.
ahclientd7.html is the page that prompts users for their passwords.
ahclientd8.html is another page that prompts users for their passwords.
These files contain %s or %d where FireWall-1 inserts information into these pages. Do not delete these symbols because unpredictable results will occur. You certainly can change where they appear, but do not change the order in which they appear. You must also keep the files less than 1,024 bytes in size.
Note that if you want to include any graphics, they need to be from a different Web server.






