The TCP Security Server
The TCP Security Server allows you to perform Content Security on any TCP service by sending the raw data stream to the CVP server. The CVP server inspects the content stream and returns the results to the TCP Security Server, which then takes the specified action in the resource. The TCP Security Server can also do URL filtering, though only the destination IP address will be sent to the UFP server.
CVP with the TCP Security Server
To have the TCP Security Server perform CVP on a particular TCP service, start by creating a new TCP Resource. From SmartDashboard/Policy Editor, select Manage and then Resources. Next select New, and choose SMTP. Or you may click on the ![]() icon in the objects tree, right-click on TCP, and select New TCP. You are presented with the window shown in Figure 9.30. Give the resource a name (tcp-virusscan is used in this example), and set the type to CVP.
icon in the objects tree, right-click on TCP, and select New TCP. You are presented with the window shown in Figure 9.30. Give the resource a name (tcp-virusscan is used in this example), and set the type to CVP.
Figure 9.30. TCP Resource Properties, General tab
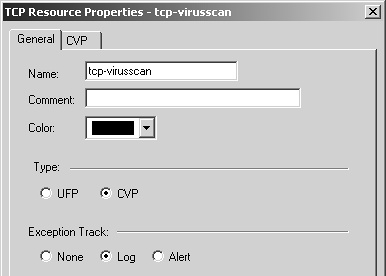
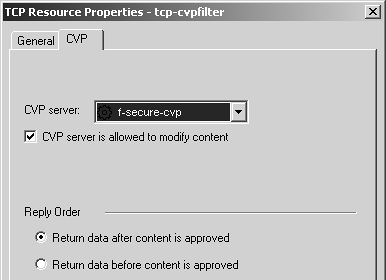
Figure 9.31 shows the CVP tab. The options here are similar to those described in the HTTP Security Server section. Once you've created the resource, edit the TCP service on which you want to enable CVP scanning. In the Advanced configuration, check the "Enable for TCP resource" box.
Figure 9.31. TCP Resource Properties, CVP tab
Create a rule similar to the one shown in Figure 9.32, and push the security policy.
Figure 9.32. Sample rule with TCP resource
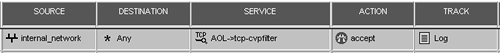
You must now configure the firewall module to listen on the TCP service port in question. For AOL, used in this example, the port is 5190. To do this, edit $FWDIR/conf/fwauthd.conf on the firewall module and add the following line to this file:
5190 fwssd in.genericd wait 0
Once you have done that, bounce the fwd process with the command fw kill fwd.
WARNING!
fw kill fwd kills the fwd process, which will prevent FireWall-1 from logging, using the Security Servers, or performing encryption tasks. The cpwatchdog process should restart fwd within a minute or so of executing this command. |
UFP with the TCP Security Server
Before proceeding with this, make sure that your UFP server can handle IP-based URLs (not all servers can).
The steps to use the TCP Security Server with UFP scanning are almost identical to the steps needed for CVP, with the following exceptions:
Create the TCP resource as type UFP instead of CVP.
You do not need to modify the firewall module to listen on the specified TCP port.






