Log Maintenance
It is recommended that you look at your logs regularly to determine whether people are attempting to violate your security policy. Also, log files themselves tend to get rather big and need to be switched every so often. In the Log Viewer application itself, you can use the New command under the File menu in the Log Viewer to rename the old log file and the Switch Active File command under the File menu to simply delete the current log, or use the command fw logswitch from the management console. Optionally, you can give fw logswitch an argument with a filename to switch the log to. The default is to simply stamp the previous fw.log file with the current date and time.
People often wish to rotate their logs daily or more frequently if logging is particularly heavy. I personally recommend doing a logswitch on a daily basis unless you log more than a few hundred thousand entries a day, in which case I would rotate at a regular interval as needed to keep the total number of log entries below 300,000.
FireWall-1 NG introduced many more options for automatically rotating log files, aside from automating this task with a cron job or the at scheduler in Windows. A gateway or management object can be configured to automatically rotate logs at a certain time or under certain circumstances. Figure 5.13 shows the configuration for a sample gateway object.
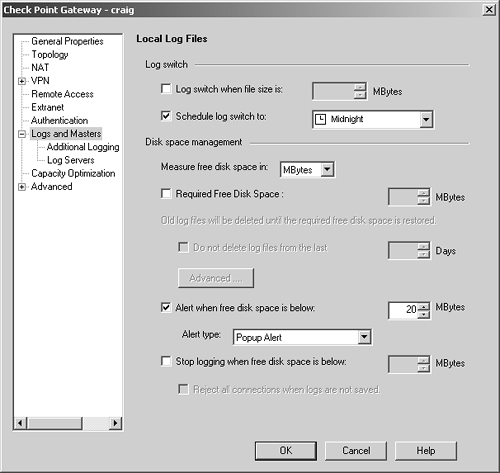
Figure 5.13. Gateway object, Logs and Masters tab
NOTE!
The following screens are relevant only on version NG objects, that is, an object for a 4.1 firewall will not show any of these options. For these systems, it is still necessary to use fw logswitch in cron or at. |
The options for the Logs and Masters tab are listed below.
Log switch when file size is: As the name implies, this automatically switches the log file when it reaches the specified size.
Schedule log switch to: This option allows you to specify a time to automatically rotate the log file. The selectable times here are defined as time objects of type scheduled event.
Measure free disk space in: Changing this option affects how the remaining options will be answered. The default is megabytes (MBytes). The other option is percent, which means free space is specified as a percentage of the overall disk space available.
Required Free Disk Space: This indicates the number of megabytes/percentage of free disk space that must be kept available. If this option is checked, the next option becomes available.
Do not delete log files from the last: This option specifies the number of days of logs that must be kept. All logs older than this will be deleted.
Advanced: This button allows you to specify a script that will run before logs are deleted. This script may, for instance, FTP the logs to a different location.
Alert when free disk space is below: This option executes the alert (indicated in the Alert type pull-down menu) when the disk space drops below the specified threshold.
Stop logging when free disk space is below: As the name implies, this option stops logging when disk space reaches the specified threshold.
Reject all connections when logs are not saved: In the unfortunate event that the system isn't saving logs, this option prevents any new connections through the firewall. Existing connections will still be permitted.
It is also possible to forward logs to other management or log servers via the Additional Logging frame (subsection of the Logs and Masters frame). Figure 5.14 shows those configuration options.
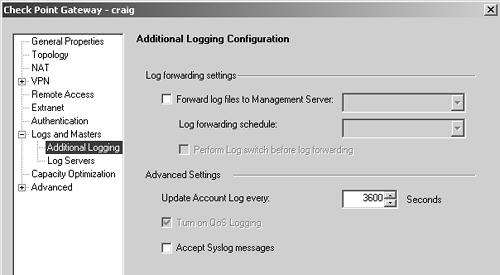
Figure 5.14. Gateway object, Additional Logging frame
The options for additional logging include those listed below.
Forward log files to Management Server: As the name implies, you can forward log files to a different management server, but you can also forward logs to a log server. Objects specified as management consoles or as log servers can be selected.
Log forwarding schedule: You must also define when this forwarding occurs by selecting a time object of type scheduled event.
Perform Log switch before log forwarding: This option performs a log switch. The log-switched file is then forwarded to the specified management server.
Update Account Log every: Any account log entries for active connections get written to the log file as frequently as this option specifies.
Turn on QoS Logging: This enables logging for FloodGate.
Accept Syslog messages: This option is present in FireWall-1 NG FP3 and later. Syslog is a remote logging mechanism used by UNIX-based platforms. This allows your module to accept syslog entries from other hosts and integrate them into the Check Point logs.
Firewall objects also have the Log Servers tab in their definition, which allows you to configure where logs are initially written. Figure 5.15 shows how this screen looks.
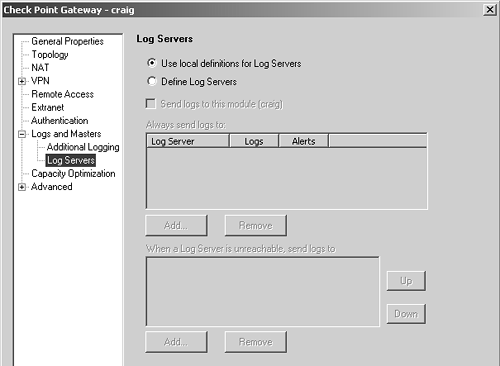
Figure 5.15. Gateway object, Log Servers frame
You can define the following options on this tab.
Use local definitions for Log Servers: This tells the firewall module to use the definitions defined in $FWDIR/conf/masters and $FWDIR/conf/loggers on the local firewall module. This also affects the Masters frame of the object, assuming it has one. This is particularly useful when the management station will be accessible only via NAT. This configuration is described in Chapter 7.
Define Log Servers: This option allows you to manually override the default logging settings.
Send logs to this module: By choosing this, you can write all logs to your local disk. If you select this option, it's recommended that you forward the logs to your management console regularly. This option won't work on systems without a local hard disk (e.g., Nokia IP71).
Always send logs to: This allows you to specify to which management console or log servers the logs are sent.
When a Log Server is unreachable, send logs to: If the primary log servers are down, use the specified alternates, in the specified order.






