Preventing Loops with Spanning Tree
STP (IEEE 802.1D) has two immediate drawbacks. The first issue is with convergence. It just takes too long for Layer 2 networks to converge. Depending on the type of failure, it could take anywhere from 30 to 50 seconds to converge the network. The other issue with STP is potential loops. Loops can be catastrophic, as discussed on numerous occasions throughout this book. Cisco introduced features such as portfast, Root Guard, and Loop Guard to help mitigate loop problems, as discussed in the next sections.
Portfast
The portfast feature skips through various stages of spanning-tree states, and it immediately brings a port from blocking to forwarding state. There are two reasons behind portfast. First, the delay incurred through normal spanning-tree states could cause startup problems. For example, a host machine's user login screen times out because the port is still transitioning through its spanning-tree states. It takes 30 seconds for a port to transition to forwarding state. While the port is transitioning, the Windows software is attempting to log on to the server and subsequently will fail because the host machine does not have full network connectivity. This problem was ubiquitous with users that had Novell Clients.
The second reason behind portfast is that Topology Change Notifications (TCNs) are not generated when a host machine joins or leaves a port. This reason is significant. If portfast is disabled on a host port, anytime a user does a restart or a shutdown on his machine, a TCN is generated by the switch and forwarded on the bridge Root Port. (See Figure 10-1.)
Figure 10-1. TCN Updates
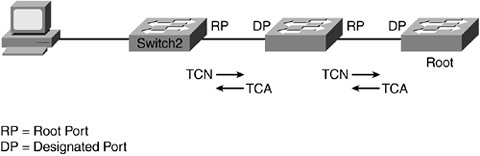
The upstream designated switch sends back a Topology Change Acknowledgment (TCA) to the switch. The process continues until the Root receives the TCN. The Root resets the content-addressable memory (CAM) entries from 5 minutes to 15 seconds (Forward delay), and the duration of the new CAM aging entry will last for 35 seconds (20 Max age + 15 Forward delay) before reverting to the 5-minute timer. The Root sends configuration bridge protocol data units (BPDUs) informing all the switches of topology and timer changes. This process is unnecessary for ports that are not participating in spanning tree. No spanning-tree change occurs when a user machine joins or leaves a bridge. As a result, portfast configuration is preferred on host ports.
Switch-to-switch links should not have portfast enabled because the switches are participating in spanning-tree topology. One small caveat exists for portfast. If the switch receives a configuration BPDU on a portfast-enabled port, it will recycle the port through the normal spanning-tree states. This protects the network from possible loops.
Example 10-1 shows how to configure portfast on host port, 3/1. A warning message is generated when portfast is enabled. The warning message reminds the engineer on what devices portfast should not be enabled.
Example 10-1. Enabling Portfast
Switch2 (enable) set spantree portfast 3/1 enable
Warning: Spantree port fast start should only be enabled on ports connected
to a single host. Connecting hubs, concentrators, switches, bridges, etc. to
a fast start port can cause temporary spanning tree loops. Use with caution.
Spantree port 3/1 fast start enabled.
The spantree command provides a global view of ports that have been enabled for portfast. (See Example 10-2.)
Example 10-2. Spanning Tree Information for VLAN 3
Switch2 (enable) show spantree 3
VLAN 3
Spanning tree mode PVST+
Spanning tree type ieee
Spanning tree enabled
Designated Root 00-05-74-18-04-80
Designated Root Priority 4099
Designated Root Cost 4
Designated Root Port 1/1
Root Max Age 20 sec Hello Time 2 sec Forward Delay 15 sec
Bridge ID MAC ADDR 00-01-63-29-bc-02
Bridge ID Priority 32768
Bridge Max Age 20 sec Hello Time 2 sec Forward Delay 15 sec
Port Vlan Port-State Cost Prio Portfast Channel_id
------------------------ ---- ------------- --------- ---- -------- ----------
3/1 3 forwarding 100 32 enabled 0
Portfast BPDU Guard
BPDU Guard goes one step further in protecting the network from possible loops. Ports enabled with portfast should not receive any BPDUs because these ports are not participating in spanning tree. Hence, any BPDUs received on these ports are invalid. Someone may have mistakenly or intentionally put a new switch on the portfast port or looped the portfast port to another switch. Portfast, by default, brings the port to blocking mode if it receives BPDU messages. It then brings the port up through the normal spanning-tree process, essentially turning off the portfast feature. The BPDU Guard feature error disables the port completely when a BPDU is heard on a portfast port. Manual intervention is required to bring the port out of error disabled (errDisabled) state. BPDU Guard is a global command that affects all the enabled portfast ports, as shown in Example 10-3.
Example 10-3. Enabling BPDU Guard
Switch2 (enable) set spantree portfast bpdu-guard enable
Spantree portfast bpdu-guard enabled on this switch
Example 10-4 illustrates a portfast BPDU Guard?enabled port receiving a BPDU message.
Example 10-4. BPDU Traffic Seen on Portfast BPDU Guard Port
Switch2 (enable) 2003 Oct 07 15:30:32 %SPANTREE-2-RX_PORTFAST: Received BPDU on
PortFast enable port. Disabling 3/1
Switch2 (enable) show port 3/1
Port Name Status Vlan Duplex Speed Type
----- -------------------- ---------- ---------- ------ ----- ------------
3/1 errdisable 3 a-half a-10 10/100BaseTX
Portfast BPDU Filter
BPDU Filter is a global command that prevents a switch from transmitting BPDU messages on a portfast-enabled port. (See Example 10-5.) Earlier in the chapter, you learned that BPDUs received on a portfast-enabled port cause the port to cycle back through its normal spanning-tree states; however, with BPDU Filter, the downstream portfast port should never see a BPDU message. BPDU is yet another safety net to prevent potential loops on a network.
Example 10-5. Enabling BPDU Filter
Switch2 (enable) set spantree portfast bpdu-filter enable
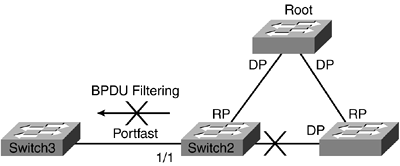
In Figure 10-2, Switch2 will not send BPDUs out its portfast port that is connected to Switch3. It will, however, continue to receive BPDU messages from Switch3. To prevent spanning-tree issues, Switch3 will also have to be enabled with BPDU filtering.
Figure 10-2. BPDU Filtering
NOTE
Note that Figure 10-2 reflects a bad design. This figure is used to illustrate BPDU filtering currently available on Cisco switches.
Root Guard
Root Guard allows a device that is connected to a portfast-enabled port to participate in spanning tree, but will not be allowed to become the root. Example 10-6 outlines Root Guard configuration.
NOTE
Root Guard is not compatible with Loop Guard, which you learn about in the next section.
Example 10-6. Enabling Root Guard
Switch2 (enable) set spantree guard root 1/1
Enable rootguard will disable loopguard if it's currently enabled on the
port(s).
Do you want to continue (y/n) [n]? y
Switch2 (enable) 2003 Oct 07 17:40:55 %SPANTREE-5-ROOTCHANGE:Root changed for
Vlan 2: New root port 0/0. New Root mac address is 00-01-63-29-bc-01.
2003 Oct 07 17:40:55 %SPANTREE-2-ROOTGUARDBLOCK: Port 1/1 tried to become non-
designated in VLAN 2. Moved to root-inconsistent state
2003 Oct 07 17:40:56 %SPANTREE-6-PORTBLK: Port 1/1 state in VLAN 2 changed to
blocking
If superior BPDUs are heard from a portfast-enabled port, the port state is changed to root inconsistent state. In Example 10-7, Switch2 heard superior BPDUs for VLAN 2 on port 1/1. Root Guard is enabled per port and affects all VLANs that traverse that port.
Example 10-7. Spanning Tree for VLAN 2
Switch2 (enable) show spantree 2
VLAN 2
Spanning tree mode PVST+
Spanning tree type ieee
Spanning tree enabled
Designated Root 00-01-63-29-bc-01
Designated Root Priority 30000
Designated Root Cost 0
Designated Root Port 1/0
Root Max Age 20 sec Hello Time 2 sec Forward Delay 15 sec
Bridge ID MAC ADDR 00-01-63-29-bc-01
Bridge ID Priority 30000
Bridge Max Age 20 sec Hello Time 2 sec Forward Delay 15 sec
Port Vlan Port-State Cost Prio Portfast Channel_id
------------------------ ---- ------------- --------- ---- -------- ----------
1/1 2 root-inconsis 4 32 enabled 0
If Switch2 stops receiving superior BPDUs on port 1/1, it will transition the port back to forwarding. (See Example 10-8.) This is a dynamic process.
Example 10-8. Port Transitioning Due to New Root
Switch2 (enable) 2003 Oct 07 17:51:07 %SPANTREE-5-MSGAGEEXPIRY: Msg Age timer expired on port 1/1 in vlan 2 2003 Oct 07 17:51:07 %SPANTREE-2-ROOTGUARDUNBLOCK: Port 1/1 restored in VLAN 2 2003 Oct 07 17:51:07 %SPANTREE-5-ROOTCHANGE:Root changed for Vlan 2: New root port 0/0. New Root mac address is 00-01-63-29-bc-01. 2003 Oct 07 17:51:07 %SPANTREE-6-PORTLISTEN: Port 1/1 state in VLAN 2 changed to listening
Loop Guard
The Loop Guard feature protects against possible spanning-tree loops by detecting a unidirectional link. With a unidirectional link, a port on one of the link partners is operationally in the up state and transmitting, but is not receiving traffic. At the same time, the other link partner is operating correctly. Loop Guard is enabled on ports that are participating in spanning tree and are redundant at Layer 2. When the switch stops receiving BPDUs on its root or blocking port, it will transition the port to loop inconsistent state, which does not pass traffic.
Loop Guard is configured per port on codes earlier than Catalyst OS 7.1(1). Loop Guard does not work with Root Guard (see Example 10-9), and Loop Guard should not be enabled on portfast ports. One other caveat involving Loop Guard is channeling. The first operational port is used for BPDUs; if the link has a unidirectional failure, Loop Guard will transition all the links off the channel to loop inconsistent state. This is not a desirable effect because the inherent redundancy gained through channeling is lost.
Example 10-9. Loop Guard Enabled
Switch2> (enable) set spantree guard loop 3/5 Enable loopguard will disable rootguard if it's currently enabled on the port(s). Do you want to continue (y/n) [n]? y Switch2> (enable) show spantree guard 3/5 Port VLAN Port-State Guard Type --------------------- ----- ------------- ---------- 3/5 2 forwarding loop
In Figure 10-3, Switch2 stops receiving BPDUs from Switch3. With Loop Guard enabled, Switch2 transitions the blocking port to loop inconsistent state. The unidirectional link could have resulted from a faulty transmit transceiver on Switch3 or a bad receive transceiver on Switch2. Regardless, Loop Guard changes the port's state to protect the network. If Loop Guard was not enabled, Switch2 would have moved the blocking port to forwarding. As result of this state change, a one-way loop would have occurred going counterclockwise. Loop Guard does not require manual intervention. If Switch2 starts hearing BPDUs again on port 3/5, it will transition the port back to blocking state.
Figure 10-3. Loop Guard








