Private VLANs
Common VLAN implementation allows for any-to-any communication. Each host on the VLAN can communicate with any other host on that segment. Preventing communication between hosts on the same VLAN requires moving the users off the VLAN to their own separate VLANs. In the past, VLANs generally had a homogenous pool of users. The users in the VLAN had some type of commonality that allowed them to share the same resources and have the same access on the network. As a result, there was no need to filter traffic between users on the same segment. For instance, vendors or contractors who needed onsite access to the customer network were typically segregated in their own VLAN. Scalability was not an issue because the number of these groups was small and manageable (see Figure 4-10).
Figure 4-10. Contractors on a Separate VLAN
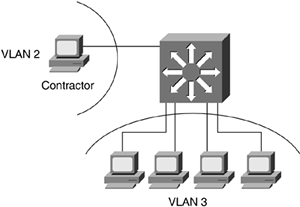
However, the numbers of these third-party groups have dramatically grown and are ubiquitous throughout the customer network, specifically government contractors. To isolate them in their own VLANs would require many IP addresses and VLANs. Figure 4-10 illustrates contractors in VLAN 2. VLAN 3 consists of company workers. Isolating contractors in their own VLANs is not practical and also would require some effort to maintain these VLANs. Private VLANs can help mitigate some of these issues. Private VLANs have the capability to restrict users on the same segment without the necessity of Layer 3 architecture. This translates to fewer IP address used and fewer new VLANs created on the network.
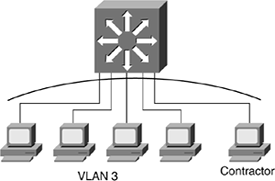
Figure 4-11 shows the contractors have been moved from VLAN 2 and are now members of VLAN 3.
Figure 4-11. Contractors on the Same VLAN
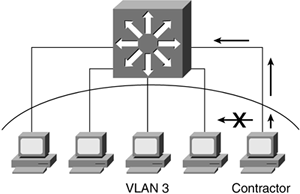
Private VLANs can also help protect hosts from each other on a segment (see Figure 4-12). Recently, corporate networks have been hit with various forms of worms. Typically, a worm infects a machine, and then it tries to form connections with other machines on the network through the infected machine. In a private VLAN environment, the infected machine has restrictions on it as to what ports it can communicate with. As a result, not all ports on that VLAN will be affected by this worm originated by the infected machine. Restrictions on a port might not give you all the protection in the world; however, as mentioned, restrictions can provide some benefits that cannot be overlooked.
Figure 4-12. Contractor Host Prevented from Communicating to Other Members on the Same VLAN
A private VLAN is an extension of the common VLAN to help restrict traffic from users on the same VLAN. It accomplishes this by assigning port designations, which include the following:
Promiscuous
Isolated
Community
Two-way community
All ports on the VLAN are assigned as part of the primary VLAN. Each port is also defined by a secondary VLAN.
The promiscuous port can communicate with any other host on the primary VLAN. It is usually the MSFC router port, Catalyst 6500 running Catalyst OS. The isolated port communicates only with the promiscuous port and no other host on the segment. It cannot communicate with other isolated ports. There can only be one isolated secondary VLAN in the primary VLAN. Community ports can communicate with the promiscuous port and other ports that are members of the community VLAN. Two different communities cannot communicate with each other.
Flows coming from the isolated or community ports are tagged internally on the switch with a secondary VLAN identifier. The identifier is used to forward the packet to the appropriate destination ports. For insolated ports, it is always going to be the promiscuous port, which internally tags all traffic destined to designated ports with primary VLAN information. If a Layer 2 access list is applied (VLAN Access List-[VACL]), the access list will only affect traffic coming from the secondary VLAN (isolated or community port) to the promiscuous port. The Layer 2 access list does not affect traffic going to the secondary VLAN because the promiscuous port will tag all traffic internally with a primary VLAN identifier. In other words, the promiscuous port cannot apply access lists going to a specific secondary VLAN. In a two-way community configuration, the router will remember the secondary VLAN information. As a result, it will be able to apply Layer 2 access list outbound to the secondary VLAN group.
Some caveats to private VLAN implementation include the following:
VTP must be configured in transparent mode.
Private VLANs can use VLANs 2-1000 and 1025-4096.
Both primary and secondary VLANs can traverse a trunk, and will participate in spanning tree. Any modifications to the primary VLAN spanning tree will affect the secondary VLAN spanning-tree algorithm.
Private VLANs cannot be configured on trunk, dynamic VLAN, or channel ports. By default, the configuration will automatically disable trunking on the port.
BPDU guard gets enabled. The BPDU guard protects against a portfast enabled port sending BPDU messages.
Internet Group Management Protocol (IGMP) snooping is not supported on the private VLANs.
The primary VLAN is 3 with two secondary VLANs, 13 and 15. These secondary VLANs have been associated with a primary VLAN with specific ports defined in Example 4-26. Then the primary and its secondary VLANs have been mapped to the promiscuous port, 15/1.
Example 4-26. Configuring Private VLANs
Switch1 (enable) set vlan 3 pvlan-type primary
Switch1 (enable) set vlan 13 pvlan-type isolated
Switch1 (enable) set vlan 15 pvlan-type twoway-community
Switch1 (enable) set pvlan 3 13 10/1
Vlan 13 configuration successful
Ports 10/1-12 trunk mode set to off.
Successfully set the following ports to Private Vlan 3,13:
10/1
Switch1 (enable) set pvlan 3 15 10/2-3
Vlan 15 configuration successful
Ports 10/1-12 trunk mode set to off.
Ports 10/1-12 trunk mode set to off.
Successfully set the following ports to Private Vlan 3,15:
10/2-3
Switch1 (enable) show pvlan
Primary Secondary Secondary-Type Ports
------- --------- ---------------- ------------
3 13 isolated 10/1
3 15 twoway-community 10/2-3
Switch1 (enable) set pvlan mapping 3 13 15/1
Successfully set mapping between 3 and 13 on 15/1
Switch1 (enable) set pvlan mapping 3 15 15/1
Successfully set mapping between 3 and 15 on 15/1
Switch1 (enable) show pvlan mapping
Port Primary Secondary
---- ------- ---------
15/1 3 13,15
Referring to Figure 4-12, the contractor now cannot communicate with Hosts1, 2, and 3. The other hosts can communicate with each other, but not with the contractor. All hosts including the contractor can communicate with the promiscuous port. Any broadcast or unicast floods generated by any of these hosts including contractor will be contained in their secondary VLAN environment. If contractor sends a broadcast message, the other hosts will not receive the broadcast message.
Private VLANs are relatively new in the enterprise network. Private VLAN offers many features, and it will become popular in the near future, especially in parts of the network where devices need to be protected from other users and possible network attacks.







