Chapter 12. Summary of Data Collection Methodology
This chapter serves two purposes. First, you can read it as a summary of the chapters in Part II to get an overview of the accounting and performance device instrumentation features. With that in mind, this chapter summarizes the high-level technical characteristics of all features discovered in the previous chapters and provides a way to structure, categorize, and compare the features.
Second, this chapter offers an entry point into the accounting and performance features. So that you won't read all the chapters and then discover that some of the accounting and performance features are not suitable for your specific scenario, the two matrixes in this chapter guide you toward the features of interest.
The previous eight chapters offer many details about the Cisco different device instrumentation features for accounting and performance management. Because the variety of functions could make it difficult to choose the "right" feature, this chapter offers you some guidance in the selection process. Two matrixes compare the features from a technical and business perspective.
Tables 12-1 and 12-2 assess the accounting and performance features described in Part II. Table 12-1 offers answers to the fundamental questions:
What to collect?
Who is the user?
How to collect (metering method)?
| Area | Data | SNMP | IP Accounting | MAC Address IP Accounting | Precedence IP Accounting | ACL IP Accounting | NetFlow | BGP PA | AAA | NBAR | IP SLA |
|---|---|---|---|---|---|---|---|---|---|---|---|
| What to collect? | DSCP/ToS | NA |  |  |  | ||||||
| MIB | NA | ||||||||||
| Memory | NA | ||||||||||
| Response time | NA |  | |||||||||
| BGP AS number | NA |  |  | ||||||||
| Applications/type | NA |  |  | ||||||||
| Availability | NA |  | |||||||||
| Session start time | NA |  |  | ||||||||
| Session stop time | NA |  |  | ||||||||
| Who is the user? | Interface counters | NA |  |  |  |  |  | ||||
| MAC address | NA |  |  | ||||||||
| IP address | NA |  |  |  |  |  | |||||
| Username | NA |  | |||||||||
| How to collect (metering method)? | Observed traffic |  |  |  |  |  |  |  |  |  | |
| Synthetic traffic |  | ||||||||||
| Sampling |  | ||||||||||
| Direction: ingress |  |  |  |  |  |  |  |  | |||
| Direction: egress |  |  |  |  |  |  |  |  |  | ||
| Originated traffic |  |  |  |  | |||||||
| Destined traffic |  |  |  |  | |||||||
| Transit traffic |  |  |  |  |  |  |  | ||||
| How to collect (collecting method)? | SNMP read |  |  |  |  |  [*] [*] |  |  [*] [*] |  |  | |
| SNMP write |  |  |  [*] [*] |  |  |  | |||||
| Security options |  |  |
[*] Partly supported
| MIB-I, II; IF-MIB | PING-MIB | PROCESS-MIB | ENVMON-MIB, MEMORY-POOL-MIB | DATA-COLLECTION-MIB | CB-QOS-MIB | FRAME-RELAY-MIB | MLS-TE-MIB | Expression and Event MIB | RMON, SMON, DSMON, ART MIB | |
|---|---|---|---|---|---|---|---|---|---|---|
| DSCP/ToS |  |  [*] [*] | ||||||||
| CPU Utilization |  |  | ||||||||
| Memory |  |  |  | |||||||
| Response Time |  |  | ||||||||
| BGP AS Number | ||||||||||
| Applications/type | ||||||||||
| Availability |  |  |  |  | ||||||
| Session Start Time | ||||||||||
| Session Stop Time | ||||||||||
| Interface Counters |  |  |  |  | ||||||
| MAC Address |  | |||||||||
| IP Address |  |
[*] Partly supported
Here are some comments for clarification:
Collection details relate to IP address, MAC address, interface counters, BGP autonomous system number, ToS/DSCP, and more. Because this is a summary table, only the most important parameters are described.
SNMP has two rows because most features support SNMP read operations but only some have writable MIB objects. Note that only a subset of available MIBs is listed.
Most features meter observed traffic, which is the actual network traffic. Metering observed traffic does not have an impact on the network traffic, compared to synthetic traffic, which is generated specifically for measurement purposes.
The session start and stop time parameters are explicitly required for billing solutions.
The metering interface (ingress or egress) and the traffic destination are distinguished. Transit traffic passes the network element and has a remote destination, whereas destined traffic targets the collection device. Originated traffic is generated at the metering device itself. Note that destined traffic can be collected only at the ingress interface and originated traffic is captured only at the egress interface. Figure 12-1 illustrates the different metering options per traffic direction.
Figure 12-1. Metering Direction and Interface
[View full size image]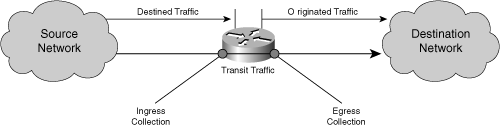
The Security Options row considers SNMPv3 as security for the listed MIBs and MD5 authentication for IP SLA.
SNMP is the protocol to transfer the MIB variables' content and therefore is independent of their type. Thus, the SNMP protocol cannot answer the questions "What to collect?" and "Who is the user?" This is why Table 12-1 shows several "not applicable" (NA) cells. These two questions are answered in Table 12-2 for the most important MIBs covered in this book.
[Pages 517 - 518]
Table 12-3 assigns accounting and performance features to the different business cases. The idea of this table is to help you choose the feature that offers exactly the level of detail you need. An alternative would be to select a feature that collects all the details and keep only the required fields. Even though this is a valid option, it is not an economical approach, because more data is collected than is actually required. For example, if you are interested in only the total amount of traffic per interface, the SNMP interface statistics provide sufficient details. Of course, alternatively you could collect all NetFlow records and aggregate the flows afterwards, but this is not suggested. Current best practice advises that you meter exactly the level of detail that fulfills your requirements.








