Chapter 27. The System.Security.Permissions Namespace
The System.Security.Permissions namespace contains permission classes and their attribute counterparts. Permissions are the mechanism through which the .NET runtime enforces code-access security. Most commonly, code uses permissions to protect access to its important functionality and resources by making security demands. A security demand raises a System.Security.SecurityException if the grant set of the calling code (and all previous callers on the call stack) does not include a permission equivalent to the one demanded. Other security operations include link demands, inheritance demands, stack walk overrides, and permission requests.
There are two ways to express security statements in code: imperative syntax and declarative syntax. Imperative syntax uses the methods of permission objects whereas declarative syntax involves the application of permission attributes to code elements, such as assemblies, classes, and methods. Permission attributes result in the instantiation and use of permission objects, but this is handled by the runtime and is transparent to both the programmer and user.
All permission classes implement the System.Security.IPermission interface, which defines the basic functionality all permissions must implement to integrate with the runtime's code-access security mechanisms. However, there are three distinct categories of permissions defined in the System.Security.Permissions namespace: code-access permissions, identity permissions, and role-based permissions. The code-access pe1rmission classes represent actions defined in, and resources accessible through, the .NET Framework class library that are subject to code-access security control. The identity permission classes represent the value of host evidence that an assembly or application domain presents to the runtime; only evidence types that implement the System.Security.Policy.IIdentityPermissionFactory have corresponding identity permission classes. The only role-based permission (PrincipalPermission) represents the identity and roles of a user on whose behalf code is running.
All of the code-access and identity permission classes extend the abstract System.Security.CodeAccessPermission base class, which implements both the System.Security.IPermission and System.Security.IStackWalk interfaces. Executing an imperative security demand for any of these permission classes involves calling their System.Security.IStackWalk.Demand( ) method, which results in a stack walk. A stack walk uses the call stack to ensure that not only the immediate caller, but also all previous caller have the demanded permission. Both the System.Security.IStackWalk interface and the System.Security.CodeAccessPermission base class define methods that allow code to manipulate the stack walk process using imperative security syntax.
Each permission class has an attribute counterpart that derives from the abstract CodeAccessSecurityAttribute class. These attribute classes allow their corresponding permission to be applied to code using declarative security syntax. Declarative security syntax provides access to a broader range of security operations than imperative syntax, including link demands, inheritance demands, and permission requests; the values of the SecurityAction enumeration represent the full range of declarative security statements. Because declarative security statements are stored as assembly metadata, the runtime and security administrators can evaluate the security requirements of an assembly without the need to load or execute the assembly. However, the content of declarative security statements are fixed at code time, and cannot be based on runtime state, or user input, unlike imperative statements. In addition, declarative security statements cannot use program constructs, such as loops and conditionals, to evaluate complex security requirements.
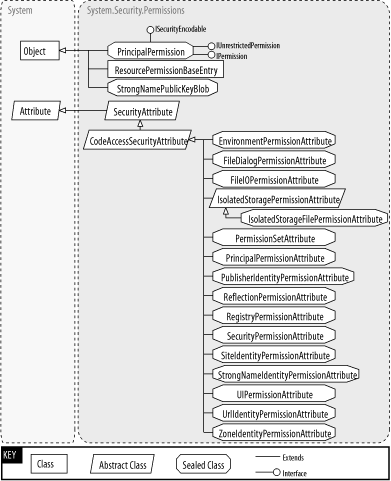
Figure 27-1 and Figure 27-1 show the types in this namespace.
Figure 27-1. CodeAccessPermissions from this namespace
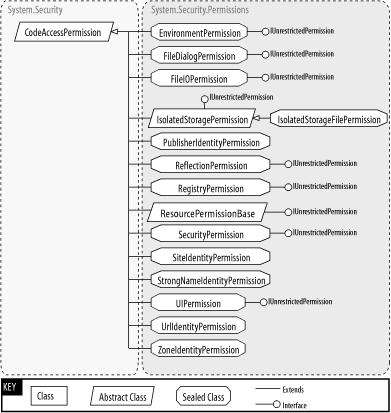
Figure 27-2. More types from this namespace