Authentication
This section covers the setup of authentication using one of the supported methods. A router can authenticate two basic modes of access:
Character mode
Packet mode
With character mode access, a user gains EXEC access to the router. This can be accomplished using one of the four lines on the router: console, auxiliary, TTY, or VTY. In packet-mode access, the user establishes a data-link layer connection by using a remote-access protocol, such as PPP, SLIP, ARAP, NASI, NetBIOS, or X.25 PAD. Because this book focuses on using a router as a firewall solution, not as a remote-access solution, this section focuses only on securing character-mode access.
Methods of Authentication
One of the first things you need to determine is how you will authenticate the different types of character-mode access. This is accomplished by using a method list, which is a sequential list of one or more authentication methods. An authentication method defines how the character mode access will be authenticated. The router processes the entries in the list in the order that you enter them. When the router successfully can use a method in the list, the other remaining methods are ignored.
For example, assume that you define two methods in your list in the following order:
TACACS+ server group aaatacgroup
Local authentication database built with username commands
With this list, the router first attempts to use the AAA servers in the TACACS+ aaatacgroup group. If the router cannot contact any of these servers, it then uses the username commands configured locally. If no username commands exist on the router, the authentication fails. As you can see from this example, you can specify multiple types of authentication in your method list, providing redundancy.
With method lists, the router attempts to use the first entry in the list. If this is not successful, it proceeds to the second entry. It is important to point out here that "unsuccessful" is not a failed authentication. In other words, if you configured AAA servers for authentication, but the servers were not reachable (do not respond back), this is unsuccessful. However, if your router can contact the servers and send the authentication information, but the AAA server denies the authentication access request, this is considered a successful authentication request (even though the user is denied access). Likewise, if you include in your method list that the router should use a local means of verifying authentication, but these commands (such as username commands, or the enable secret or line password commands) do not exist on the router, then when the router tries to use these methods, it considers them unsuccessful and proceeds to the next method in the list.
NOTE
As with ACLs, if the router attempts to use all of the methods in the list but is unsuccessful, the router automatically denies the authentication request.
Now take a look at Figure 5-2, another example that clarifies the use of method lists.
Figure 5-2. Authentication Method List Example
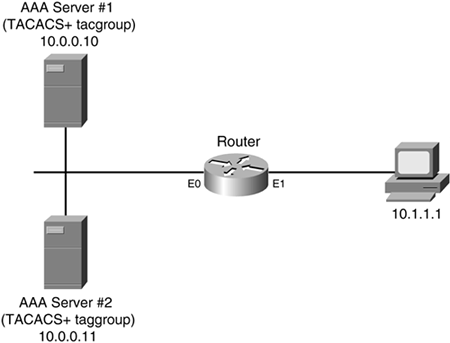
In this example, 10.1.1.1 is trying to gain EXEC access to the router. Here is the method list defined to perform authentication for EXEC access:
TACACS+ server group tacgroup.
Local authentication database built with the username richard secret quizware command.
In the first method, there are two AAA servers in the TACACS+ group tacgroup: 10.0.0.10 and 10.0.0.11. The second method defines one local username command for an account called richard.
When 10.1.1.1 tries to gain EXEC access, based on the methods configured on the router, the Cisco IOS first tries to contact AAA server 1 (10.0.0.10) to perform authentication. If this server is reachable, neither the other AAA server, nor the other method in this list, is used. Instead, 10.1.1.1 must put in a correct username/password combination that is found on the AAA server. If the user does not, the user fails authentication and is denied access to the router.
Assume that AAA server 1 has failed, though. In this situation, when 10.1.1.1 tries to access EXEC mode on the router, the Cisco IOS still uses the tacgroup method first. It attempts to contact the first AAA server; because this server is not reachable, it then attempts to contact the second server. If the second server is also not reachable, only then is the second method in the list used. In this example, because one username command is defined, the 10.1.1.1 user must put in this correct username/password combination to gain access to the router's EXEC mode. If I had forgotten to configure any username commands, and the Cisco IOS was attempting to use the second method, the Cisco IOS would realize that because no username commands were configured, it should go to the third method in the list. Because there is no third method defined in this example, the user automatically is denied access.
NOTE
Basically three types of statuses are shown in the previous example:
Success? The method was available, and the user was authenticated.
Fail? The method was available, but the user was not able to authenticate.
Error? One of two things occurred:
- The first AAA server in the group of the specified method was not reachable, so the next server in the group was used.
- The method specified either does not exist, or, with an AAA server group, all of the servers are not reachable.
Authentication Configuration
Now that you have a basic understanding of method lists, take a look at the command used to configure AAA authentication: aaa authentication. The following sections expand on the use of this command.
User EXEC Authentication
Two types of authentication are discussed in this chapter for AAA: gaining access to a user and privileged EXEC shell, commonly referred to as login authentication and enable authentication, respectively. This section and the next section cover these two types of authentication.
To secure user EXEC shell access, you need to use at least the first two commands listed:
Router(config)# aaa new-model Router(config)# aaa authentication login {default | list_name} method1 [method2...] Router(config)# line [aux | console | tty | vty] start_line_# [end_line_#] Router(config-line)# login authentication {default | list_name} Router(config-line)# timeout login response seconds
As you already know, the aaa new-model command enables AAA. You must execute this command before you can configure any other AAA commands on the router. The aaa authentication login command is used to secure EXEC access to the router.
Following the login parameter is the name of the authentication reference. The Cisco IOS uses this parameter so that the appropriate aaa authentication login command is used for the type of access that a person is using to gain access to a line (an EXEC shell). The default parameter specifies that this default authentication method command should be used if a line does not specify which aaa authentication login command to use. You can create specific authentication methods by entering aaa authentication login, followed by a unique name to the authentication method, as in telnet-access. You then go into the appropriate line or lines, as shown in the bottom two commands in the previous syntax. Next, you specify the list name AAA authentication method that should be used with the login authentication command, followed by the list name found in the aaa authentication login command, as in telnet-access. Note that, on all lines, the default list is default, so the Cisco IOS uses the aaa authentication login default command's method list to verify authentication.
The last, and most important, part of the aaa authentication login command is the list of methods. Remember from the previous section that the method list defines how authentication should be done. You can list up to four methods. A list of valid methods is found in Table 5-2. These methods are processed in the order that you specify. Remember that if a method produces an error result, the next method in the list is used.
Method Keyword | Description |
|---|---|
enable | The password in the enable secret or enable password commands is used to perform the authentication. |
line | The line password command, on the line that the user is trying to access, is used to perform authentication. |
local | The username commands are used to perform authentication. |
local-case | The username commands are used to perform authentication. However, the username that the user enters is treated as case sensitive. |
none | No authentication is performed. |
group radius | All configured RADIUS servers can be used to perform authentication. |
group tacacs+ | All configured TACACS+ servers can be used to perform authentication. |
group group_name | Only servers in the specified aaa group server command are used to perform authentication. |
CAUTION
I highly recommend that you not use the none method for authentication, even if you list multiple methods and this is the last one, creating a back door into the router. Always perform some type of authentication, even if it is something as simple as using the enable or line passwords. Some hackers try to exploit a DoS attack against the router and AAA servers if you are using AAA servers as a method, hoping that your second method defined on the router is none. This would allow the hacker to sneak into your router by preventing the router and AAA servers from communicating with each other.
The timeout line command specifies the number of seconds that the Cisco IOS waits for login information before timing out the authentication. The default is 30 seconds, but this can range from 1 to 300 seconds.
Privileged EXEC Authentication
To secure privilege EXEC access, you need to use the following command:
Router(config)# aaa authentication enable default method1 [method2...]
Unlike the aaa authentication login command, the aaa authentication enable command does not allow you to specify authentication lists?you can use only the keyword default. This makes sense because there is only one way to access privileged EXEC mode: Execute the enable command from user EXEC mode. With user EXEC mode access, a user can gain access in many ways, such as with the console, auxiliary, VTY, and TTY lines. With the aaa authentication login command, you can set up different authentication methods for these. However, this is not necessary for privileged EXEC access because there is only one way to access it.
You can list four AAA methods in your method list for securing privileged EXEC access. These are the same ones shown previously in Table 5-2; however, the local and local-case methods are not supported with privileged EXEC authentication.
Username and Password Prompts
By default, when the Cisco IOS prompts you for a username or password when you log in, you see the following prompts:
Username: Password:
You can override these default prompts with the following two commands:
Router(config)# aaa authentication username-prompt prompt_string Router(config)# aaa authentication password-prompt prompt_string
The aaa authentication username-prompt command overrides the username prompt and enables you to specify your own prompt for the username. The aaa authentication password-prompt command enables you to change the password prompt presented to the user. Remember to add the : to the end of the prompt; it is not included automatically.
TIP
Sometimes I set the username prompt to Password: and leave the password prompt as the same thing. At first, this looks confusing because, even though the first prompt states "password," it actually wants the username. I do this to confuse hackers and users trying to gain unauthorized access. Just tell authorized users that no matter what they see in the prompts, they need to enter the username for the first prompt and the password for the second prompt.
NOTE
TACACS+ and RADIUS servers have the capability to override the username and password prompts. If you have configured the aaa authentication username-prompt and password-prompt commands, and have also configured these prompts on your AAA servers, the Cisco IOS uses the prompts from the AAA servers.
Login Banners
If you have enabled AAA, you can override the router's default login banner with the following command:
Router(config)# aaa authentication banner stop_character message stop_character
This command works the same as the banner command discussed in Chapter 3. The actual message can be up to 2996 characters in length. When you enter the aaa authentication banner command, the router displays this banner instead of the banner created with the banner command.
Optionally, you can display a message whenever a user enters an invalid username/password combination by configuring the following command:
Router(config)# aaa authentication fail-message stop_character message stop_character
With this command, whenever the user enters an invalid username/password combination, the Cisco IOS displays the configured message. The actual message can be up to 2996 characters in length.
Login Attempts
By default, the Cisco IOS prompts you for username/password information up to three times so that you can enter the correct information. After three times, the Cisco IOS disconnects you and forces you to attempt to log in again. With AAA, you can change the number of login attempts before the router disconnects you with the following command (this is new in Cisco IOS 12.2T):
Router(config)# aaa authentication attempts login #_of_attempts
The number of login attempts can range from 1 to 25.
TIP
For a perimeter router, I recommend that you set this value to 1. This makes it more cumbersome for someone to execute an access attack against it, especially a brute-force password attack.
Authentication Troubleshooting
You use one basic command for troubleshooting AAA authentication problems: debug aaa authentication. Example 5-5 shows output from the debug aaa authentication command.
Example 5-5. Using the debug aaa authentication Command
Router# debug aaa authentication
13:21:20: AAA/AUTHEN: create_user user='' ruser='' port='tty6' (1)
rem_addr='10.0.0.32' authen_type=1 service=1 priv=1
13:21:20: AAA/AUTHEN/START (0): port='tty6' list='' (2)
action=LOGIN service=LOGIN
13:21:20: AAA/AUTHEN/START (0): using "default" list (3)
13:21:20: AAA/AUTHEN/START (70215483): Method=TACACS+
13:21:20: TAC+ (70215483): received authen response
status = GETUSER
13:21:20: AAA/AUTHEN (70215483): status = GETUSER
13:21:23: AAA/AUTHEN/CONT (70215483): continue_login
13:21:23: AAA/AUTHEN (70215483): status = GETUSER
13:21:23: AAA/AUTHEN (70215483): Method=TACACS+
13:21:23: TAC+: send AUTHEN/CONT packet
13:21:23: TAC+ (70215483): received authen response
status = GETPASS
13:21:23: AAA/AUTHEN (70215483): status = GETPASS
13:21:27: AAA/AUTHEN/CONT (70215483): continue_login
13:21:27: AAA/AUTHEN (70215483): status = GETPASS
13:21:27: AAA/AUTHEN (70215483): Method=TACACS+
13:21:27: TAC+: send AUTHEN/CONT packet
13:21:27: TAC+ (70215483): received authen response
status = PASS
13:21:27: AAA/AUTHEN (70215483): status = PASS (4)
The following is an explanation of Example 5-5. The numbers on the right side of Example 5-5 correspond to the numbers in the following list:
A remote user from 10.0.0.32 attempts to log in to the router.
The router checks to see if login authentication services are enabled; they are.
The router sees that the default list method is used, and the corresponding method is TACACS+ (the line below this).
After authentication takes place, the TACACS+ server responds with a successful authentication message (status = PASS).
Authentication Example
Now that you have a basic understanding of how to configure authentication for AAA, take a look at an authentication example in Example 5-6.
Example 5-6. AAA Authentication Example
Router(config)# aaa new-model (1) Router(config)# tacacs-server host 10.0.0.10 single-connection (2) key secret10 Router(config)# tacacs-server host 10.0.0.11 single-connection key secret11 Router(config)# aaa group server tacacs aaatacgroup (3) Router(config-sg)# server 10.0.0.10 Router(config-sg)# server 10.0.0.11 Router(config)# aaa authentication login console (4) group aaatacgroup local Router(config)# username admin1 secret cisco1 Router(config)# username admin2 secret cisco2 Router(config)# aaa authentication login default (5) group aaatacgroup Router(config)# aaa authentication enable default (6) group aaatacgroup enable Router(config)# enable secret OutKeep Router(config)# aaa authentication username-prompt "Password: " (7) Router(config)# aaa authentication password-prompt "Password: " Router(config)# aaa authentication attempts login 1 (8) Router(config)# line console 0 Router(config-line)# login authentication console (9)
The following is an explanation of Example 5-6. The numbers on the right side of Example 5-6 correspond to the numbers in the following list:
This command enables AAA.
These two commands specify the two TACACS+ servers used for authentication.
These three commands are not really necessary in this example, but I like to set up groupings for future use.
This command sets up a user EXEC authentication method called console, and it has two methods in its method list: Use the TACACS+ servers in the aaatacgroup (group aaatacgroup) and username commands (local). This statement is referenced in number 9, which authenticates console access. Note that I used the word console as a descriptive term; you can use anything that you want to describe this authentication method.
This command is the default authentication method for user EXEC access. It specifies that only the TACACS+ servers are used for authentication. If these servers are not available, the user is not allowed access to the router. This command can be used to authenticate VTY access because there is no reference to the type of authentication list that should be used on the VTY lines.
This command authenticates access to privileged EXEC mode. It has two methods for authentication: the TACACS+ server grouping and the enable command, listed below this statement.
These two statements are used to confuse or trick people performing access attacks: It changes the username prompt to match that of the password prompt.
This command restricts the number of access attempts to one for a session. If the user cannot successfully authenticate on the first try, the session is terminated, and the user must re-establish the session to try again.
This command references the aaa authentication login console command, which specifies how authentication should be done on the console line.








