AP Examples
Now that you have a basic understanding of how to set up AP, I use a couple of examples to illustrate the configuration of AP. The next two sections cover these examples.
Simple AP Example
This first example uses a simple network with simple policies (see Figure 14-3). This example concerns only outside-to-inside access (the next example throws in NAT and CBAC, to make the scenario more complex). This example wants to allow outside access to the public services, but it requires authentication through HTTP to access the private services. Note that the private file server does not support HTTP; therefore, external users must authenticate by using HTTP to connect to the private web server.
Figure 14-3. Simple AP Example
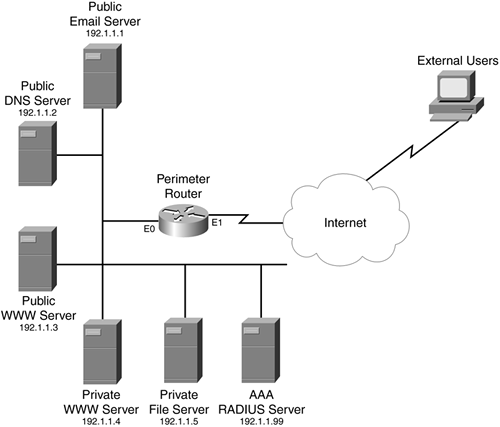
Example 14-9 displays the configuration for the router in Figure 14-3.
Example 14-9. A Simple AP Configuration Example
Router(config)# aaa new-model (1) Router(config)# radius-server host 192.1.1.99 key cisco (2) Router(config)# aaa authentication login default group radius (3) Router(config)# aaa authentication login console-override group radius enable Router(config)# aaa authorization exec default group radius (4) Router(config)# aaa authorization auth-proxy default (5) group radius Router(config)# ip http server (6) Router(config)# ip http authentication aaa (7) Router(config)# ip auth-proxy inactivity-timer 10 (8) Router(config)# ip auth-proxy name check-outside http (9) list check-these Router(config)# ip access-list extended check-these (10) Router(config-ext-nacl)# permit tcp any host 192.1.1.4 eq www Router(config-ext-nacl)# deny ip any any Router(config-ext-nacl)# exit Router(config)# ip access-list extended protect (11) Router(config-ext-nacl)# permit tcp any host 192.1.1.4 eq www Router(config-ext-nacl)# permit tcp any host 192.1.1.1 eq smtp Router(config-ext-nacl)# permit udp any host 192.1.1.2 eq dns Router(config-ext-nacl)# permit tcp any host 192.1.1.3 eq www Router(config-ext-nacl)# deny ip any any Router(config-ext-nacl)# exit Router(config)# interface ethernet1 Router(config-if)# ip access-group protect in (12) Router(config-if)# ip auth-proxy check-outside (13) Router(config-if)# exit Router(config)# line console 0 Router(config-line)# login authentication console-override (14) Router(config-line)# exit Router(config)# enable secret ocsic
Here is an explanation of this example, with reference to the numbering on the right side of Example 14-9:
This enables AAA.
This defines the RADIUS server used for AAA.
This enables login authentication, which is required for AP. However, two commands are used. The first command provides the default method for authentication: RADIUS. The second command is used for console access (see Statement 14) and has a backup method (the privileged EXEC password) if the RADIUS server is not available.
If a user is authenticated, only specific authorized users can gain EXEC access to the router. In other words, I do not want to allow external AP users to access the EXEC shell of the router; instead, I define the list of authorized users on the RADIUS server.
CAUTION
It is important that you use this aaa authorization command. You definitely do not want any authenticated user access to the shell. AP users should be allowed access only to other services, not the EXEC shell on the router itself.
Authorization for AP is enabled by using RADIUS?if the RADIUS server is not reachable, the AP users are denied access.
This enables the router's HTTP server function.
This enables AAA authentication for the HTTP server function.
This changes the idle timeout for AP cached information from 60 to 10 minutes.
This defines the AP policy: Only HTTP connections listed in the ACL called check-these (see Statement 10) are authenticated. This is important because I want to verify access to the private servers, but I do not want to use AP for the public server.
This defines which connections require AP (only those to the private web server).
This defines access from the outside world to the inside resources. Notice two things: You must allow the AP connection (the first entry in the ACL), and you should deny anything else, including access to the private file server (this is allowed by the UAP defined on the RADIUS server).
This activates the external ACL inbound on the external interface.
This activates the AP policy on the external interface.
This overrides the default authentication method on the console (below this is the encrypted privileged EXEC password used as the second login method for the console port (see the statement immediately after no. 3).
AP and EXEC AccessAs I mentioned in the last Caution note, you always should configure AAA authorization for EXEC access. I once dealt with a client who did not do this. Its configuration allowed users to access an IP address on the router to perform the authentication; however, after authenticating, the user was presented with the user EXEC interface for the router through the web browser. Obviously, this is a serious security risk. When I learned this, I immediately changed the configuration to authorize EXEC access, preventing the AP users from gaining any type of access to the router, with the exception of the AP authentication component. We defined a few exceptions for network administrators within CiscoSecure ACS for Windows 2000. |
Complex AP Example: CBAC and NAT
This example uses a more complicated setup in which the router is performing CBAC and NAT, as well as AP. The network in this example is shown in Figure 14-4. In this example, NAT is required because the internal resources are using a private address space: 192.168.1.0/24. Also, CBAC is used to provide a stateful firewall function. For the internal users, all users must be authenticated through HTTP before they can access the Internet: This can be done through an HTTP connection to the router or through an HTTP connection to any Internet web server. Per-user downloadable ACLs are configured on the RADIUS server, defining what specific user groups are allowed to access on the Internet. External users automatically can access the public servers; however, to access the private servers, they first must authenticate through AP by connecting to the private internal web server.
Figure 14-4. Complex AP Example
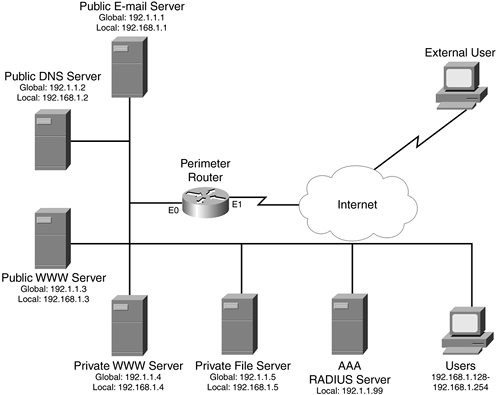
Example 14-10 displays the configuration for the network shown in Figure 14-4.
Example 14-10. AP Example with CBAC and NAT
Router(config)# ip inspect name CBAC-leaving http (1) Router(config)# ip inspect name CBAC-leaving ftp Router(config)# ip inspect name CBAC-leaving realaudio Router(config)# ip inspect name CBAC-leaving smtp Router(config)# ip inspect name CBAC-leaving streamworks Router(config)# ip inspect name CBAC-leaving udp Router(config)# ip inspect name CBAC-leaving tcp Router(config)# Router(config)# ip inspect name CBAC-entering http (2) Router(config)# ip inspect name CBAC-entering ftp Router(config)# ip inspect name CBAC-entering realaudio Router(config)# ip inspect name CBAC-entering smtp Router(config)# ip inspect name CBAC-entering streamworks Router(config)# ip inspect name CBAC-entering udp Router(config)# ip inspect name CBAC-entering tcp Router(config)# Router(config)# ip nat inside source static (3) 192.168.1.0 192.1.1.0 /24 Router(config)# Router(config)# aaa new-model (4) Router(config)# radius-server host 192.1.1.99 key cisco (5) Router(config)# aaa authentication login default group radius (6) Router(config)# aaa authentication login console-override group radius enable Router(config)# aaa authorization exec default group radius (7) Router(config)# aaa authorization auth-proxy default (8) group radius Router(config)# Router(config)# ip http server (9) Router(config)# ip http authentication aaa (10) Router(config)# ip auth-proxy inactivity-timer 60 (11) Router(config)# ip auth-proxy name check-outside http (12) list external-AP Router(config)# ip auth-proxy name check-inside http (13) list internal-AP Router(config)# Router(config)# ip access-list extended external-AP (14) Router(config-ext-nacl)# permit tcp any host 192.1.1.4 eq www Router(config-ext-nacl)# deny ip any any Router(config-ext-nacl)# exit Router(config)# Router(config)# ip access-list extended internal-AP (15) Router(config-ext-nacl)# permit tcp 192.168.1.128 0.0.0.127 any eq www Router(config-ext-nacl)# deny ip any any Router(config-ext-nacl)# exit Router(config)# Router(config)# ip access-list extended protect-from-inside (16) Router(config-ext-nacl)# permit tcp 192.168.1.128 0.0.0.127 any eq www Router(config-ext-nacl)# deny ip 192.168.1.128 0.0.0.127 any Router(config-ext-nacl)# permit host ip 192.168.1.1 any eq smtp Router(config-ext-nacl)# deny ip any any Router(config-ext-nacl)# exit Router(config)# Router(config)# ip access-list extended protect-from-outside (17) Router(config-ext-nacl)# permit tcp any host 192.1.1.4 eq www Router(config-ext-nacl)# permit tcp any host 192.1.1.1 eq smtp Router(config-ext-nacl)# permit udp any host 192.1.1.2 eq dns Router(config-ext-nacl)# permit tcp any host 192.1.1.3 eq www Router(config-ext-nacl)# deny ip any any Router(config-ext-nacl)# exit Router(config)# Router(config)# interface ethernet0 Router(config-if)# description **Inside Interface** Router(config-if)# ip access-group protect-from-inside in (18) Router(config-if)# ip auth-proxy check-inside (19) Router(config-if)# ip inspect CBAC-entering out (20) Router(config-if)# ip nat inside (21) Router(config-if)# exit Router(config)# Router(config)# interface ethernet1 Router(config-if)# description **Outside Interface** Router(config-if)# ip access-group protect-from-outside in (22) Router(config-if)# ip auth-proxy check-outside (23) Router(config-if)# ip inspect CBAC-leaving out (24) Router(config-if)# ip nat outside (25) Router(config-if)# exit Router(config)# Router(config)# line console 0 Router(config-line)# login authentication console-override (26) Router(config-line)# exit Router(config)# enable secret ocsic (27)
Here is an explanation of this example, with reference to the numbering on the right side of Example 14-10:
This defines the CBAC inspection rule for traffic leaving the network. This is activated on the external interface (ethernet1) in the outbound direction (Statement 24).
This defines the CBAC inspection rule for traffic entering the network. This is activated on the internal interface (ethernet0) in the outbound direction (Statement 20).
This creates the static translations for the inside private (local) addresses to public (global) addresses: 192.168.1.0/24 to 192.1.1.0/24.
This enables AAA.
This defines the AAA RADIUS server.
This defines authentication for login and console access (console access has a second method, the privileged EXEC password).
This defines authorization for EXEC access, thereby restricting AP users from gaining EXEC access on the router. This authorization needs to be defined on the AAA server and should permit only network administrators.
This enables AP authorization for AAA through RADIUS.
This enables the HTTP server on the router.
This enables HTTP authentication for AP users.
This increases the AP idle timer to 60 minutes.
This creates an AP policy for external users. HTTP is used for the authentication method, and only access to the private web server triggers authentication (external-AP ACL, defined in Statement 14).
This creates an AP policy for internal users. HTTP is used for the authentication method, and only internal users (192.168.1.128 to 192.168.1.255) are authenticated (internal-AP, defined in Statement 15). Additional downloadable ACLs can be created for the users' groups to restrict external access.
This defines when AP occurs for external users accessing the private web server.
This defines when AP occurs when internal users access the Internet.
This allows internal devices access to the Internet. The first ACL statement admits the AP. The second statement denies everything else from internal users. However, downloadable ACLs defined on the AAA server can allow users access to other resources. The third statement in the ACL allows the e-mail server to send e-mails to other e-mail servers. This ACL is activated in ethernet0 in the inbound direction (see Statement 18).
This filters traffic from the Internet as it enters this network. The first statement allows the AP process to take place to the public server. The next three statements allow external users to the public servers?web, DNS, and e-mail.
This activates the ACL that blocks internal traffic from leaving the network.
This activates the internal AP policy about restricting internal users from accessing Internet resources.
This activates the CBAC inspection rule that allows Internet traffic back through the inside interface as it is sent from internal servers as a reply to external user requests.
This specifies the inside interface for NAT.
This activates the external ACL on the external interface, blocking Internet traffic.
This activates the external AP policy to authenticate users from the Internet.
This activates the CBAC inspection rule that allows returning traffic to the Internet.
This specifies the outside interface for NAT.
This overrides the default AAA login authentication rule to use for console access.
This configures the privileged EXEC password, which is used as the second authentication method for console access if the RADIUS server is not reachable.
TIP
As you can see from this example, when you start adding more features to your router's configuration, your task becomes more complex. In this example, I highly recommend that you do the configuration in small pieces. In this example, configure NAT first and then the ACLS, then CBAC, and finally AP.







