BGP Security
This section focuses on securing BGP. In most cases, BGP is used in large networks with two or more Internet connections, where the company needs to have control of traffic leaving and (sometimes) entering the network. One of the issues with BGP is that it does not behave very well in unstable environments. In other words, when there are a lot of changes within BGP, the router must spend a lot of processing to deal with the changes. Without any type of security measures, an ingenious hacker could hijack an external or internal BGP session and wreak havoc on your BGP routing protocol. A hacker easily can generate a DoS attack to subvert your routing information or overcome your router's resources with flapping route information.
As with the IGPs, BGP supports router authentication with MD5. Authentication can be used to prevent spoofing attacks. Another tool, although not security related, is route dampening. In times of heavy routing update changes, you want to ensure that your router is not swamped with handling changes. With a DoS attack, your router might begin missing BGP keepalives, which could cause routing confusion. Route dampening can help with this problem. I discussed bogon filtering at the beginning of this chapter, but BGP also supports this function through the use of prefix lists; with prefix lists, you can restrict what BGP routes your router will accept from a neighbor or neighbors. The following three sections deal with these topics.
Authentication
Of all the routing protocols, setting up MD5 authentication with BGP is the easiest. After you have set up BGP with your peer router and are sending and receiving routes, you should add the following statement to both routers:
Router(config)# router bgp AS_# Router(config-router)# neighbor neighbor's_IP_address password password
As you can see from this example, setting up authentication is very easy. Just make sure that the password is the same on both routers; otherwise, neither router will accept each other's routing updates. The password can be of mixed case and can be up to 80 characters in length. The first character in the password cannot be a number or a space; however, this is permitted with subsequent characters. MD5 authentication is used to verify the entire BGP TCP segment: This ensures that no tampering is done with the routing updates and routing information contained in the TCP segment.
TIP
When you enable MD5 authentication, the existing TCP connection between the peers is torn down and then rebuilt. Do this during a time of little activity on the router.
CAUTION
Remember my earlier warning about using MD5 authentication and sending routing updates through devices that change packet header information. For BGP, this would invalidate the BGP routing updates between peers.
Route Flap Dampening
BGP route flap dampening is a feature that you can enable on your router that helps it during a time of BGP convergence. With route flap dampening, BGP is more stable and requires fewer CPU cycles when dealing with flapping routes. A flapping route is a route that constantly fluctuates, causing a BGP router to generate update messages (adding and withdrawing the flapping route or routes). Every smart ISP already should be doing this with BGP configurations.
To set up BGP route flap dampening, add the following command to your BGP configuration:
Router(config)# router bgp AS_# Router(config-router)# bgp dampening [half_life] [reuse] [suppression_limit] [maximum_suppression_time] [route-map route_map_name]
Table 15-2 explains the optional parameters for the bgp dampening command. Even though each of these values is optional, all are position-dependent (with the exception of the route-map parameter). Therefore, if you want to change the reuse value, you first must enter the half_life value. To display statistics about flapping routes, use the show ip bgp flap-statistics command. To display dampened BGP routes, use the show ip bgp dampened-paths command.
Parameter | Values | Explanation |
|---|---|---|
half_life | 1 to 45 minutes (the default is 15) | Determines how fast the accumulated penalty for a route can decay exponentially, eventually allowing it to be used again. After a route becomes stabilized, the penalty for the route is reduced by half after each half-life period expires. When the penalty value falls below the reuse threshold, the route is used again. |
reuse | 1 to 20,000 (the default is 750) | When the penalty value for the route falls below this threshold, it is used again by BGP. |
suppression_limit | 1 to 20,000 (the default is 2000) | When a route is assigned a penalty that exceeds this value, the route is suppressed (dampened). |
maximum_suppression_time | 1 to 255 minutes (the default is four times the half_life parameter value) | This is the maximum amount of time that a route can be suppressed, regardless of the number of times that the route flaps. |
route_map_name | Name of route map | This controls which routes BGP dampening is or is not used for. |
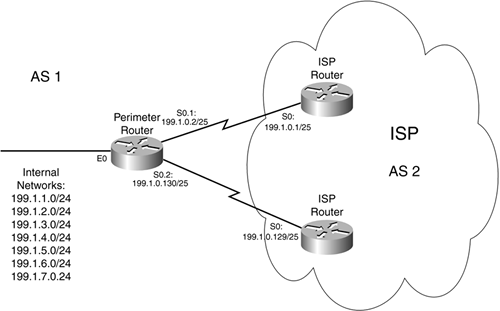
To help you better understand the process of route dampening, assume that there is a network connected to an ISP using BGP, like that shown in Figure 15-4. In this example, 199.1.7.0/24 is flapping, and the perimeter router has route dampening enabled. When the route flaps enough that its penalty exceeds the configurable suppression limit, the perimeter router stops advertising the route to the ISP. This penalty is decayed using the half-life timer until the reuse limit is reached. When that limit is reached, the perimeter router begins advertising the route again.
Figure 15-4. BGP Dampening Example
NOTE
When you have configured route dampening and a BGP peer is reset, the route or routes are withdrawn, but no penalty is applied to the routes. Also, routes external to an AS that were learned from an IBGP peer never are dampened.
BGP Routing Example
To help you better understand how to configure BGP on a router securely, I use the example shown in Figure 15-4 to illustrate a simple solution. The Team Cymru Web Site has an excellent example of setting up BGP in a secure fashion at http://www.cymru.com/Documents/secure-bgp-template.html. Example 15-15 is based on this template and is used to secure BGP running on the perimeter router in Figure 15-4.
Example 15-15. Securing a BGP Router
Router(config)# router bgp 1 Router(config-router)# no synchronization (1) Router(config-router)# no bgp fast-external-fallover (2) Router(config-router)# bgp log-neighbor-changes (3) Router(config-router)# bgp dampening route-map (4) varied-dampening Router(config-router)# network 199.1.0.0 mask 255.255.248.0 (5) Router(config-router)# Router(config-router)# neighbor 199.1.0.1 remote-as 2 (6) Router(config-router)# neighbor 199.1.0.1 (7) soft-reconfiguration inbound Router(config-router)# neighbor 199.1.0.1 password as2router1 (8) Router(config-router)# neighbor 199.1.0.1 version 4 (9) Router(config-router)# neighbor 199.1.0.1 prefix-list (10) bogonlist in Router(config-router)# neighbor 199.1.0.1 prefix-list (11) announce_out out Router(config-router)# neighbor 199.1.0.1 (12) maximum-prefix 163000 75 Router(config)# Router(config-router)# neighbor 199.1.0.129 remote-as 2 (13) Router(config-router)# neighbor 199.1.0.129 soft-reconfiguration inbound Router(config-router)# neighbor 199.1.0.129 password as2router2 Router(config-router)# neighbor 199.1.0.129 version 4 Router(config-router)# neighbor 199.1.0.129 prefix-list bogonlist in Router(config-router)# neighbor 199.1.0.129 prefix-list announce_out out Router(config-router)# neighbor 199.1.0.129 maximum-prefix 163000 75 Router(config-router)# no auto-summary (14) Router(config-router)# exit Router(config)# Router(config)# ip route 199.1.0.0 255.255.248.0 null0 (15) Router(config)# ip route 199.1.1.0 255.255.255.0 ethernet0 (16) Router(config)# ip route 199.1.2.0 255.255.255.0 ethernet0 Router(config)# ip route 199.1.3.0 255.255.255.0 ethernet0 Router(config)# ip route 199.1.4.0 255.255.255.0 ethernet0 Router(config)# ip route 199.1.5.0 255.255.255.0 ethernet0 Router(config)# ip route 199.1.6.0 255.255.255.0 ethernet0 Router(config)# ip route 199.1.7.0 255.255.255.0 ethernet0 Router(config)# Router(config)# ip prefix-list announce_out description only (17) advertise our summarized route Router(config)# ip prefix-list announce_out seq 5 permit 199.1.0.0/21 Router(config)# ip prefix-list announce_out seq 10 deny 0.0.0.0/0 le 32 Router(config)# Router(config)# ip prefix-list bogonlist description (18) Block bogons Router(config)# ip prefix-list bogonlist seq 5 deny 0.0.0.0/8 le 32 Router(config)# ip prefix-list bogonlist seq 10 deny 1.0.0.0/8 le 32 Router(config)# ip prefix-list bogonlist seq 15 deny 2.0.0.0/8 le 32 Router(config)# ip prefix-list bogonlist seq 20 deny 5.0.0.0/8 le 32 Router(config)# ip prefix-list bogonlist seq 25 deny 7.0.0.0/8 le 32 Router(config)# ip prefix-list bogonlist seq 30 deny 10.0.0.0/8 le 32 Router(config)# ! <--other bogons omitted, but you would keep on listing them here--> Router(config)# ip prefix-list bogonlist seq 900 (19) permit 0.0.0.0/0 le 27 Router(config)# Router(config)# ip prefix-list dampen_long_prefixes (20) description /24 prefixes longer. Router(config)# ip prefix-list dampen_long_prefixes seq 5 permit 0.0.0.0/0 ge 24 Router(config)# Router(config)# ip prefix-list dampen_medium_prefixes (21) description /22 and /23 prefixes Router(config)# ip prefix-list dampen_medium_prefixes seq 5 permit 0.0.0.0/0 ge 22 le 23 Router(config)# Router(config)# ip prefix-list dampen_short_prefixes (22) description /21 prefixes and shorter Router(config)# ip prefix-list dampen_short_prefixes seq 5 permit 0.0.0.0/0 le 21 Router(config)# Router(config)# ip prefix-list DNS_root_servers (23) description DNS root server addresses Router(config)# ip prefix-list DNS_root_servers seq 5 permit 198.41.0.0/24 Router(config)# ip prefix-list DNS_root_servers seq 10 permit 128.9.0.0/16 Router(config)# ip prefix-list DNS_root_servers seq 15 permit 192.33.4.0/24 Router(config)# ip prefix-list DNS_root_servers seq 20 permit 128.8.0.0/16 Router(config)# ip prefix-list DNS_root_servers seq 25 permit 192.203.230.0/24 Router(config)# ip prefix-list DNS_root_servers seq 30 permit 192.5.4.0/23 Router(config)# ip prefix-list DNS_root_servers seq 35 permit 192.112.36.0/24 Router(config)# ip prefix-list DNS_root_servers seq 40 permit 128.63.0.0/16 Router(config)# ip prefix-list DNS_root_servers seq 45 permit 192.36.148.0/24 Router(config)# ip prefix-list DNS_root_servers seq 50 permit 193.0.14.0/24 Router(config)# ip prefix-list DNS_root_servers seq 55 permit 198.32.64.0/24 Router(config)# ip prefix-list DNS_root_servers seq 60 permit 202.12.27.0/24 Router(config)# Router(config)# route-map varied-dampening deny 10 (24) Router(config-route-map)# match ip address prefix-list DNS_root_servers Router(config-route-map)# exit Router(config)# route-map varied-dampening permit 20 (25) Router(config-route-map)# match ip address prefix-list dampen_long_prefixes Router(config-route-map)# set dampening 30 750 3000 60 Router(config-route-map)# exit Router(config)# route-map varied-dampening permit 30 (26) Router(config-route-map)# match ip address prefix-list dampen_medium_prefixes Router(config-route-map)# set dampening 15 750 3000 45 Router(config-route-map)# exit Router(config)# route-map varied-dampening permit 40 (27) Router(config-route-map)# match ip address prefix-list dampen_short_prefixes Router(config-route-map)# set dampening 10 1500 3000 30 Router(config-route-map)# exit Router(config)# Router(config)# ip access-list extended allow_BGP_updates (28) Router(config-ext-nacl)# ! <--insert other ACL statements--> Router(config-ext-nacl)# permit tcp host 199.1.0.1 host 199.1.0.2 eq 179 Router(config-ext-nacl)# permit tcp host 199.1.0.1 eq 179 host 199.1.0.2 Router(config-ext-nacl)# permit tcp host 199.1.0.129 host 199.1.0.130 eq 179 Router(config-ext-nacl)# permit tcp host 199.1.0.129 eq 179 host 199.1.0.130 Router(config-ext-nacl)# access-list 185 deny tcp any any eq 179 log-input Router(config-ext-nacl)# ! <--insert other ACL statements--> Router(config-ext-nacl)# exit Router(config)# interface serial0.1 point-to-point (29) Router(config-subif)# ip access-group allow_BGP_updates in Router(config-subif)# exit Router(config)# interface serial0.2 point-to-point Router(config-subif)# ip access-group allow_BGP_updates in Router(config-subif)# exit
The following is an explanation of the configuration in Example 15-15, with reference to the numbering on the right side of the configuration:
Does not wait for the IGP to catch up with convergence.
Allows for occasional missed keepalives.
Logs events regarding BGP neighbors.
Specifies the route map to use for dampening. This performs different types of dampening, based on the route in question. These are covered in Statement 23.
Reduces CPU utilization by using a network statement to advertise the route, along with a null route statement (later) that prohibits the use of the summarized statement by the router itself; it uses the more specific routes. See Statement 16.
Configures neighbor 1 in AS 2.
Prevents a complete withdrawal of all prefixed routes for neighbor 1 when the clear ip bgp command is used, speeding up convergence.
Defines the MD5 BGP password, which is used for authentication.
Disables negotiation of the BGP version, which speeds up the peering process.
Blocks all bogon advertisements in BGP routing updates. These are shown in Statement 18.
TIP
Prefix lists have replaced distribution lists as the preferred filter for BGP on Cisco routers because they are easier on the router's CPU.
Restricts the advertisement of routes to the ISP, and also prevents the router from becoming a transit network.
Prevents the router from trying to receive too many routes from the peer router, causing it to crash. The limit here is a maximum limit (163,000 routes), and 75 is the percentage point at which the Cisco IOS starts generating log messages, indicating a possible problem.
This is neighbor 2's configuration, which is basically the same as that of neighbor 1.
Disables router auto-summarization.
Ensures that the summarized route for the internal network is not used if it is the only route.
Involves configuring your internal routing protocol; for a network this small, I am using static routes that point to the appropriate internal network. Obviously, for more than one internal router connected to the perimeter router, you would specify the next-hop address instead of the interface.
Uses a prefix list that restricts the router to advertising only the 199.1.0.0/21 summarized route. See Statement 5. Notice that BGP uses prefix lists.
Prevents the router from advertising bogon networks. Notice that BGP uses prefix lists.
Restricts summarized routes to a /27 or smaller prefix. This ensures that your router is not flooded with more specific routes. Note that you might need to adjust this value to something smaller (less than 27) for a router with smaller memory. If you need more specific paths to make more intelligent choices about reaching a destination, you might need to adjust this to a larger value (greater than 27). This is different for every situation and router.
Specifies a prefix list of routes with a prefix of 24 bits or longer. This is used to set up special dampening for the prefixes in Statement 25 (longer prefixes are dampened longer than shorter ones).
Specifies a prefix list of routes with a prefix between Statements 22 and 23. This is used to set up special dampening for the prefixes in Statement 26.
Specifies a prefix list of routes with a prefix of 21 or less. This is used to set up special dampening for the prefixes (which tend to be more stable) in Statement 27.
Specifies a prefix list of DNS root server addresses. This is used for special dampening of these prefixes, ensuring that you do not dampen these. See Statement 24.
Ensures that the DNS root servers are never dampened, even if their routes are flapping. Historically, these routes have been stable. See Statement 23.
Specifies dampening for /24 and greater prefixes to 60 minutes. See Statement 20.
Specifies dampening for /22 to /23 prefixes to 45 minutes. See Statement 21.
Specifies dampening for /21 prefixes and smaller to 30 minutes. See Statement 22.
Creates an ACL to allow BGP traffic. You need to insert statements before and after these statements. Notice that these statements allow communication only between this router and the two ISP peer routers in AS 2. It is also important to point out that this ACL is an example: No other traffic would be allowed through this ACL, so you would need to tune it appropriately.
Activates the ACL on the two point-to-point serial links.
As you can see from this example, setting up BGP, along with security, on your perimeter router is not a task for the faint of heart: It is a very complicated process that requires intimate knowledge of BGP.








