NAT and CBAC Example
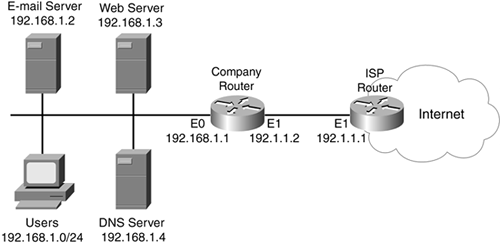
Now that you have a basic understanding of NAT, let us talk about how you would use CBAC?or, for that matter, any type of filtering on a router that also has NAT configured on it. In Figure 11-10, the network is using a private address space (192.168.1.0/24), and the ISP has assigned it a Class C public address space: 192.1.1.0/24. However, one restriction of the use of this address space is that two of these addresses must be used for the perimeter router's Ethernet1 connection to the ISP router (192.1.1.1 and 192.1.1.2). Also, the internal network has three services that it wants to allow external users to access: a DNS server, a web server, and an e-mail server.
Figure 11-10. NAT, CBAC, and Filtering Example
NOTE
To simplify matters, assume that the DNS server is using split DNS. With split DNS, the DNS server has two (or more) sets of resolution entries. Based on the source of the DNS query, the DNS server sends back a specific resolution. In this example, when internal devices request resolution for internal services, the DNS server sends back the appropriate private address (192.168.1.0/24) in the reply. However, when external devices request resolution for internal services, the DNS server sends back the corresponding public address for the service (the one configured through static NAT on the router). This is a common approach to dealing with the use of public and private addresses along with address translation.
In this example, assume that all unnecessary services have been disabled (this was covered in Chapter 4, "Disabling Unnecessary Services"). I use static NAT for the internal services and dynamic NAT for the internal users. Example 11-14 focuses primarily on the configuration for ACL filtering, CBAC, and NAT on the company router.
Example 11-14. Using ACLs, CBAC, and NAT on a Perimeter Router
Router(config)# ip route 0.0.0.0 0.0.0.0 192.1.1.1 Router(config)# Router(config)# ip inspect name allow-back-in ftp (1) Router(config)# ip inspect name allow-back-in http Router(config)# ip inspect name allow-back-in realaudio Router(config)# ip inspect name allow-back-in smtp Router(config)# ip inspect name allow-back-in tcp Router(config)# ip inspect name allow-back-in udp timeout 20 Router(config)# ip inspect name allow-back-in vdolive Router(config)# Router(config)# ip nat inside source static 192.168.1.2 192.1.1.12 (2) Router(config)# ip nat inside source static 192.168.1.3 192.1.1.13 Router(config)# ip nat inside source static 192.168.1.4 192.1.1.14 Router(config)# Router(config)# ip nat pool inside-nat 192.1.1.20 192.1.1.254 (3) netmask 255.255.255.0 Router(config)# ip nat inside source list 1 pool inside-nat Router(config)# access-list 1 permit 192.168.1.0 0.0.0.255 Router(config)# Router(config)# access-list 100 deny (4) Router(config)# ! <--list of boguns and others should be placed here--> Router(config)# access-list 100 permit icmp any 192.1.1.0 0.0.0.255 unreachable Router(config)# access-list 100 permit icmp any 192.1.1.0 0.0.0.255 echo-reply Router(config)# access-list 100 permit icmp any 192.1.1.0 0.0.0.255 packet-too-big Router(config)# access-list 100 permit icmp any 192.1.1.0 0.0.0.255 time-exceeded Router(config)# access-list 100 permit icmp any 192.1.1.0 0.0.0.255 administratively-prohibited Router(config)# access-list 100 permit tcp any host 192.1.1.12 eq 25 Router(config)# access-list 100 permit tcp any host 192.1.1.13 eq 80 Router(config)# access-list 100 permit udp any host 192.1.1.14 eq 53 Router(config)# access-list 100 deny ip any any Router(config)# Router(config)# interface Ethernet0 Router(config-if)# ip address 192.168.1.1 255.255.255.0 Router(config-if)# ip nat inside Router(config-if)# exit Router(config)# interface Ethernet1 Router(config-if)# ip address 192.1.1.2 255.255.255.0 Router(config)# ip access-group 100 in Router(config)# ip nat outside Router(config)# ip inspect allow-back-in out (5)
Refer to the numbers on the right side of Example 11-14 for the following explanation of the configuration. In this example, Statement 1 sets up the inspection for CBAC and then is activated outbound on the external interface, ethernet1, in Statement 5. In Statement 2, three static NAT translations are set up for the e-mail, web, and DNS servers. In Statement 3, these three commands set up dynamic NAT for the inside users. Statement 4 filters ingress traffic from the Internet?I put in a placeholder (a comment with the !) for filtering bogun, private IP, and other addresses. Refer to Chapter 7, "Basic Access Lists," for information on configuring these ACL entries. I then allow certain ICMP messages and traffic to the three internal servers. Everything else is denied. Note that the global addresses are used in the ACL statements, not the addresses that these servers actually have assigned on them. Also, notice that I have enabled NAT on the inside (ethernet0) and outside (ethernet1) interfaces.
As you can see from this example, setting up NAT with other Cisco IOS features is not that difficult. However, one important point to make about this example is that, when you set up filters, you always should use the addresses that show up in the packet headers. For example, notice that in the ingress filter on ethernet1, I specified the destination addresses as the public addresses; this is because the Cisco IOS processes the ACL before it performs NAT:
For the outside interface, filter on the global addresses.
For the inside interface, filter on the local addresses.
Also notice that you can use unused addresses off a router's interface for your address translation. In this example, I used unused addresses from 192.1.1.0/24, which is connected to ethernet1. In this instance, the router answers all ARP requests to 192.1.1.0/24 addresses that it has in its address-translation table, basically spoofing or proxying the responses. In this situation, make sure that you do not disable proxy ARP on the router's external (E1) interface.







