Setting Up IEEE 802.11b Wireless Ethernet Networks
Setting Up IEEE 802.11b Wireless Ethernet Networks
If you have laptop computers on your LAN or if you don't want to run wires to connect a PC to the LAN, you have the option of using a wireless Ethernet network. In a typical scenario, you have a cable modem or DSL connection to the Internet, and you want to connect one or more laptops with wireless network cards to access the Internet through the cable or DSL modem. This section shows you how to set up wireless networking for connecting to an Ethernet LAN and accessing the Internet.
Understanding Wireless Ethernet Networks
There are two popular IEEE standards-802.11a and 802.11b-for wireless Ethernet networks, also commonly referred to Wi-Fi (for Wireless Fidelity) networks. These two standards were finalized in 1999, and they specify how the wireless Ethernet network works at the physical level.
| Insider Insight |
To learn more about wireless Ethernet, visit http://www.wi-fi.org/, the home page of the Wi-Fi Alliance-a nonprofit international association formed in 1999 to certify interoperability of wireless LAN products based on IEEE 802.11 standards. |
Understanding Infrastructure and Ad Hoc Modes
The 802.11 standard defines two modes of operation for wireless Ethernet networks: infrastructure and ad hoc. Ad hoc mode is simply two or more wireless Ethernet cards communicating with each other without an access point.
Infrastructure mode refers to the approach in which all the wireless Ethernet cards communicate with each other and to the wired LAN through an access point. For the example considered in this book, your wireless Ethernet card should be set to infrastructure mode. In the configuration files, this mode is referred to as Managed mode.
Understanding Wired Equivalent Privacy (WEP)
The 802.11 standard includes the Wired Equivalent Privacy (WEP) for protecting wireless communications from eavesdropping. WEP relies on a 40-bit or 104-bit secret key that is shared between a mobile station (such as a laptop with a wireless Ethernet card) and an access point (also called a base station). The secret key is used to encrypt packets before they are transmitted and an integrity check is performed to ensure that packets are not modified in transit. The 802.11 standard does not explain how the shared key is established. In practice, most wireless LANs use a single key that is shared between all mobile stations and access points. Such an approach, however, does not scale well to an environment such as a college campus due to the fact that the keys are shared with all users. Therefore, WEP is typically not used on large wireless networks such as the ones at universities. In such wireless networks, users should other security approaches such as using SSH (Secure Shell) to log in to remote systems.
To counter against these weaknesses, WEP uses some defenses:
-
Integrity Check (IC) Field-To make sure that data packets are not modified in transit, WEP uses an Integrity Check field in each packet.
-
Initialization Vector (IV)-To avoid encrypting two messages with the same key stream, WEP uses a 24-bit initialization vector (IV) that augments the shared secret key to produce a different RC4 key for each packet. The IV itself is also included in the packet.
Experts say that both of these defenses are poorly implemented, making WEP ineffective. The problems with IC and IV are the following:
-
The Integrity Check field is implemented using a checksum algorithm called 32-bit cyclic redundancy code (CRC-32), and that checksum is then included as part of the data packet. Unfortunately, it is possible for an attacker to flip arbitrary bits in an encrypted message and correctly adjust the checksum so that the resulting message appears valid.
-
The 24-bit IV is sent in the clear. This means that there are only 224 possible initialization vectors, and they have to be reused after running through all of them. In other words, after sending 224, or 16,777,216 packets, the IV has to be repeated. The number might sound like a lot, but consider the case of a busy access point that sends 1,500-byte packets at a rate of 11 Mbps. Each packet has 8x1,500 = 12,000 bits. That means each second the access point sends 11,000,000/12,000 = 916 packets. At that rate, the access point sends 16,777,216 packets in 16,777,216/916 = 18,315 seconds or 5 hours. That means the IV is reused after 5 hours, and the time may be less than that because many message are smaller than 1,500 bytes. Thus, there are ample opportunities for an attacker to collect two encrypted messages that are encrypted with the same key stream and perform statistical attacks to decrypt the message.
Thus, WEP has its weaknesses, but it's better than nothing. You can use it in smaller wireless LANs where sharing the same key among all wireless stations is not an onerous task.
| Insider Insight |
There is work underway to provide better security than WEP for wireless networks. The 802.11i standard, which is under development, would use public key encryption with digital certificates and an an authentication, authorization, and accounting RADIUS (Remote Authentication Dial-In User Service) server to provide better security for wireless Ethernet networks. While the 802.11i standard is in progress, the Wi-Fi Alliance-a multivendor consortium that supports Wi-Fi-is publishing an interim specification called Wi-Fi Protected Access (WPA) that's a precursor to 11i. WPA will replace the existing WEP standard and improve security by making some changes. For example, unlike WEP, which uses fixed keys, the WPA standard uses Temporal Key Integrity Protocol (TKIP), which generates new keys for every 10K of data transmitted over the network. This makes WPA more difficult to break. |
Setting Up the Wireless Hardware
To set up the wireless connection, you need a wireless access point and a wireless network card in each PC. You can also set up an ad hoc wireless network among two or more PCs with wireless network cards, but that would be a wireless LAN among those PCs only. In this section, I focus on the scenario where you want to set up a wireless connection to an established LAN that has a wired Internet connection through a cable modem or DSL.
In addition to the wireless access point, you would also need a cable modem or DSL connection to the Internet, along with a NAT router/hub, as described in the previous sections. Figure 13-7 shows a typical setup for wireless Internet access through an existing cable modem or DSL connection.
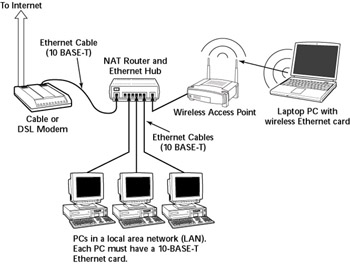
Figure 13-7: Connecting a Mixed Wired and Wireless Ethernet LAN to the Internet.
As Figure 13-7 shows, the LAN has both wired and wireless PCs. In this example, a cable or DSL modem connect the LAN to the Internet through a NAT router/hub. A wireless access point is attached to one of the RJ-45 ports on the hub. Laptops with wireless network cards connect the LAN through the wireless access point. To connect desktop PCs to the wireless network, you can use a USB wireless network card-a wireless network card that connects to a USB port.
| Cross Ref |
See Appendix F for a brief discussion of PCMCIA wireless network cards supported by Red Hat Linux. |
| Insider Insight |
If you have not yet purchased a NAT router/hub for your cable or DSL connection, consider buying a router/hub that has a built-in wireless access point. |
Configuring the Wireless Access Point
Configuring the wireless access point involves the following:
-
Setting the frequency or channel on which the wireless access point communicates with the wireless network cards. Both the access point and cards must use the same channel.
-
Whether encryption is to be used or not.
-
If encryption is to be used, the number of bits in the encryption key and the value of the encryption key. Twenty-four bits of the encryption key are internal to the access point; you only specify the remaining bits of the encryption key. Thus, for 64-bit encryption, you have to specify a 40-bit key, which comes to 10 hexadecimal digits (a hexadecimal digit is one of 0 through 9 and the letters A through F). For a 124-bit encryption key, you specify 104 bits, or 26 hexadecimal digits.
-
Setting the access method that wireless network cards would use when connecting to the access point. The choices are open access and shared key. You typically use the open access method (even when you use encryption).
-
Setting the wireless access point to operate in infrastructure mode because that's the way you should connect wireless network cards to an existing Ethernet LAN.
Insider Insight The exact method of configuring the wireless access point depends on the make and model of the access point. The vendor provides the instructions to configure the wireless access point. You would typically work through a graphical client application to configure the wireless access point. If you enable encryption, make a note of the encryption key because you have to specify the same key for each wireless network card.
Configuring Wireless Networking
On your Red Hat Linux laptop, the PCMCIA or PC Card manager should recognize the wireless network card and load the appropriate driver for the card. The wireless network card is treated like another Ethernet device and assigned a device name such as eth0 or eth1. If you already have an Ethernet card in the laptop, that card gets the eth0 device name, and the wireless PC card is named the eth1 device.
|
Parameter |
Description |
|---|---|
|
BOOTPROTO |
The name of the protocol to use to get the IP address for the interface. Should be either dhcp or bootp for Ethernet interface. |
|
CHANNEL |
Channel number (between 1 and 14 in U.S. and Canada). Must be the same as that set for the wireless access point. |
|
DEVICE |
The device name for the wireless Ethernet network interface (eth0 for the first interface, eth1 for second, and so on) |
|
ESSID |
Extended Service Set (ESS) Identifier, also known as the wireless network name. It is case sensitive and must be the same as the name specified for the wireless access point. Provide the name within single quotes (for example, 'Home'). |
|
HWADDR |
The hardware address (also called the MAC address) of the wireless network card (six pairs of colon-separated hexadecimal numbers; for example, 00:02:2d:8c:f9:c4) |
|
KEY |
Encryption key; 10 hexadecimal digits for 40-bit key (for example, 1fdf-3fde-fe) or 26 hexadecimal digits for 104-bit key. The keys are in fact 64-bit and 128-bit, but the encryption algorithm automatically generates 24 bits of the key, so you need to specify only the remaining bits. |
|
MODE |
The mode of operation of the wireless network card. Set to Managed for a typical network that connects through a wireless access point. |
|
NAME |
A nickname for your wireless network. If you don't specify it, the hostname is used as the nickname. |
|
ONBOOT |
Set to yes to activate the wireless interface at boot time; otherwise set to no. |
|
PEERDNS |
Set to yes to enable the interface to modify your system's /etc/resolv.conf file to use the DNS servers obtained from the DHCP server (this is the same server that provides the IP address for the interface). If you set this to no, the /etc/resolv.conf file is left unchanged. |
|
RATE |
Bit rate for the wireless connection (set to one of 1M, 2M, 5.5M, 11M, or auto). The M means Mbps or a million bits per second. Set to auto to use the maximum possible transmission rate. |
|
TYPE |
Set to Wireless for wireless network interface |
|
USERCTL |
When set to yes, a nonroot user can control the device. Set it to no so that only root can control the device. |
Now, the wireless interface should be working properly. To check the interface status, type the following command:
iwconfig
Here's a typical output on my Red Hat Linux laptop:
lo no wireless extensions.
eth0 IEEE 802.11-DS ESSID:"Test-Network" Nickname:"localhost.localdomain"
Mode:Managed Frequency:2.437GHz Access Point: 00:30:AB:06:2F:4E
Bit Rate:11Mb/s Tx-Power=15 dBm Sensitivity:1/3
RTS thr:off Fragment thr:off
Encryption key:AABB-CCDD-EE
Power Management:off
Link Quality:40/92 Signal level:-57 dBm Noise level:-97 dBm
Rx invalid nwid:0 Rx invalid crypt:0 Rx invalid frag:0
Tx excessive retries:0 Invalid misc:4221 Missed beacon:0
Here the eth0 interface refers to the wireless network card. I have edited the encryption key and some other parameters, but the sample output shows what you should see when the wireless link is working.







