Internet Connectivity Through Firewalls
Many customers of the service provider will not want to associate their VPN routes with Internet routes and will require that connectivity between the Internet and the VPN sites be through a security device such as a firewall. This dictates that the VPN routes are held in separate routing tables to the Internet routes, or that firewalls are present in every VPN site that wants to access the Internet directly across the backbone.
If Internet access is obtained through the MPLS/VPN backbone using any method other than central site Internet access (with one or more central sites), it is necessary for firewalls to be present at each site so that any traffic between the Internet and the VPN site will pass through the firewall. If this access is provided in a hub-and-spoke arrangement, such as central site Internet access, then not all sites require firewall services because these can be present within the central site.
This requirement is typical of Internet access from the enterprise. In this type of VPN environment, where customer sites are linked through PVCs/SVCs or IP tunnels, it is normal for Internet access to be provided through certain sites. Each site sends its Internet traffic to one or more central sites, and this traffic passes through a firewall within the central site. In the case of MPLS/VPN, in which the customer site imports a default route that is generated by one of the service provider routers, no firewall service will be available for the traffic to traverse (unless a firewall is present between the customer site and the provider backbone).
Figure 12-20. Internet Access Through CE Running Cisco IOS Firewall Feature Set Software
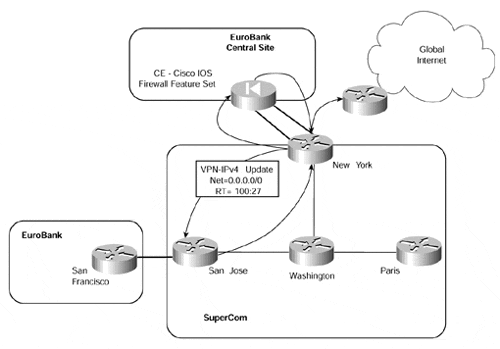
Figure 12-20 shows a topology in which Internet access for all EuroBank sites is obtained through the EuroBank's central site. This central site is capable of providing firewall services between members of the VPN and the Internet. VPN members forward their Internet traffic toward the central site because they have imported a default route with a particular route target that has been generated by the central site.
In this sample topology, the firewall service is provided through the use of the Cisco Secure Integrated software (formerly known as the Cisco IOS Firewall Feature Set) on the CE-router. This is obviously not the only possible topology; it is equally possible to house the firewall services away from the CE-router.
Two (sub)interfaces, which we will see in more detail later, have been utilized. One interface is associated with the VRF; the other is associated with the global routing table. This means that any traffic from a VPN member that follows the default route will pass through the PE-router, across the VRF interface to the CE-router, and then back up to the PE-router across the second interface. The PE-router will then route the traffic based on its global routing table.








