Summary
VPNs can be classified in a variety of ways. The broadest technological classification is based on the way the routing information is exchanged in the VPN. In the peer-to-peer VPN model, the customer routing information is exchanged between the customer routers and the service provider routers. In the overlay VPN model, the service provider provides only VCs (logical leased lines) and the routing information is exchanged directly between the edge customer routers. The two models can be combined in a large service provider network: The peer-to-peer VPN model might use overlay VPN in its access parts (for example, connecting customers to the provider edge routers through Frame Relay) or its core (for example, linking provider routers through ATM).
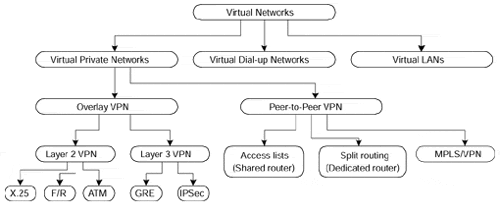
The more detailed VPN classification (displayed in Figure 7-25) focuses on the underlying technology that is used to transport Layer 3 packets over the VPN. The overlay VPN model can be implemented with Layer 2 WAN switching technologies (X.25, Frame Relay, SMDS, or ATM) or Layer 3 tunneling technologies (IP-over-IP, IPSec). The peer-to-peer VPN model can be implemented traditionally with complex routing tricks or IP access lists, both having a number of shortcomings outlined in the section, "Peer-to-peer VPN Model." The Multiprotocol Label Switching (MPLS)?based VPNs, described in the following chapters, overcome most of the shortcomings of other peer-to-peer VPN technologies, allowing the service providers to combine the benefits of the peer-to-peer model (simpler routing, simpler implementation of customer requirements) with the security and the isolation inherent in the overlay VPN model.
Figure 7-25. VPN Classification Based on Underlying Technology